折腾:
【未解决】小花生中如何得到getToken的计算逻辑以便得到正确的md5值可以正常请求接口
期间,已经试了:
【已解决】用基于Procyon的Luyten反编译安卓jar包得到java源码
和
【已解决】用Procyon命令行去从jar包导出java源代码
不过打算继续试试,别人也常提到CFR,看看效果如何。
看了介绍
“CFR – another java decompiler
CFR will decompile modern Java features – up to and including much of Java 9, 10, 12 and beyond, but is written entirely in Java 6, so will work anywhere! (FAQ) – It’ll even make a decent go of turning class files from other JVM langauges back into java!
To use, simply run the specific version jar, with the class name(s) you want to decompile (either as a path to a class file, or as a fully qualified classname on your classpath). (–help to list arguments).
Alternately, to decompile an entire jar, simply provide the jar path, and if you want to emit files (which you probably do!) add –outputdir /tmp/putithere”
-》其用法倒是和Procyon很类似
-》也是只支持 单个jar文件整个导出
也是要指定输出文件夹
等等
去试试
CFR=Class File Reader
下载
然后再去包含了要解析的jar包的文件夹中去:
1 | java -jar /Users/crifan/dev/dev_tool/android/reverse_engineering/CFR/cfr-0.141.jar -jar com.huili.readingclub.jar --outputdir readingclub_CFR |
即可:
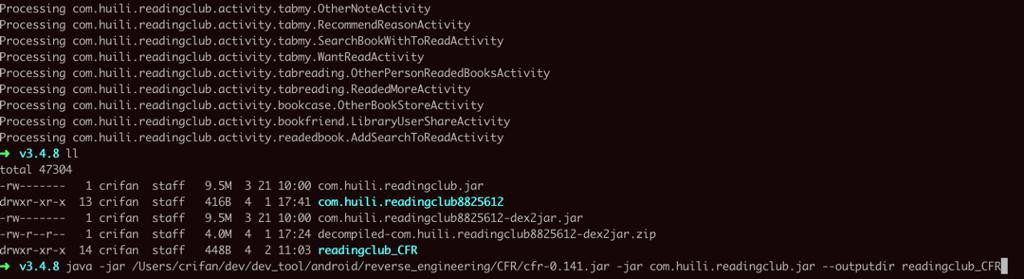
注:反编译期间,也是CPU占用率非常高的
然后即可输出得到源码,其中还有个summary:
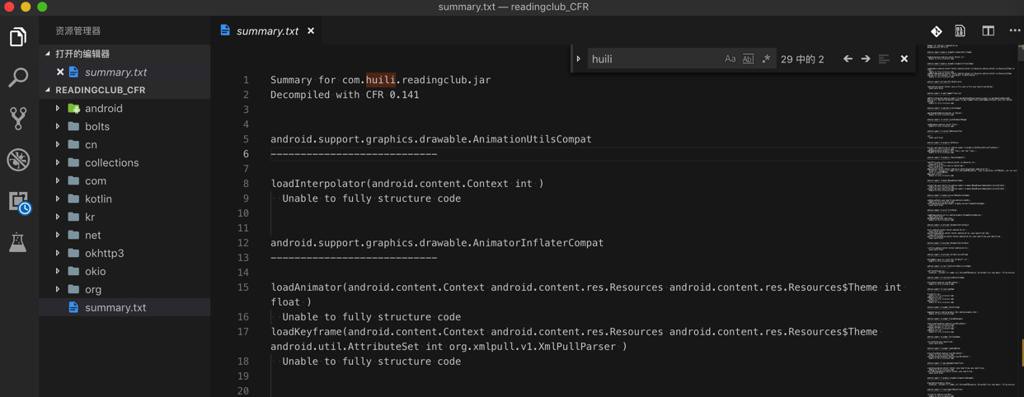
而简单看了下,发现对于我们希望的那个函数:
com.huili.readingclub.model.ModelSecurity的getToken
竟然也出错了:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 | Summary for com.huili.readingclub.jarDecompiled with CFR 0.141android.support.graphics.drawable.AnimationUtilsCompat----------------------------loadInterpolator(android.content.Context int ) Unable to fully structure code...com.huili.readingclub.model.ModelSecurity----------------------------getToken(java.lang.String ) Loose catch blockrun() Loose catch block |
不过看源码,实际上是可以解析出源码的,虽然提示有点小问题:
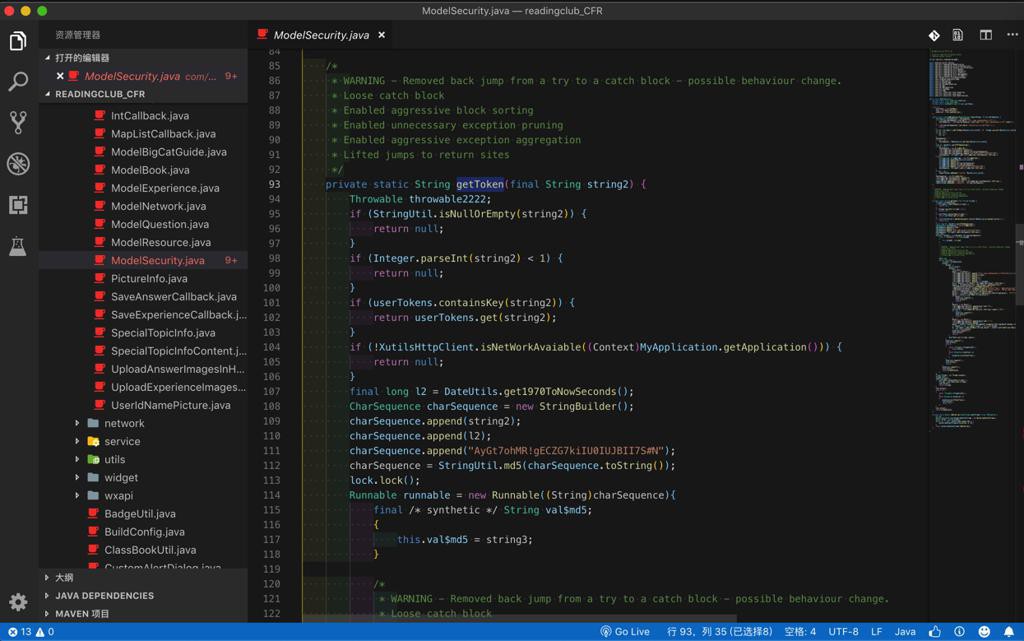
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 | * WARNING - Removed back jump from a try to a catch block - possible behaviour change. * Loose catch block * Enabled aggressive block sorting * Enabled unnecessary exception pruning * Enabled aggressive exception aggregation * Lifted jumps to return sites */ private static String getToken(final String string2) { ... ... lock.lock(); Runnable runnable = new Runnable((String)charSequence){ ... /* * WARNING - Removed back jump from a try to a catch block - possible behaviour change. * Loose catch block * Enabled aggressive block sorting * Enabled unnecessary exception pruning * Enabled aggressive exception aggregation * Lifted jumps to return sites */ @Override public void run() { Throwable throwable2222; block11 : { block9 : { Object object; block10 : { lock.lock(); object = new Object(); |
-》所以,这个CFR也还是不错的。
【总结】
此处,用CFR=Class File Reader去反编译jar包,导出java源代码的步骤是:
2.命令行运行,从某个jar包,反编译导出整个java源码
语法:
1 | java -jar /path_to_your_cfr/cfr-0.141.jar -jar your_to_decompile.jar --outputdir output_folder_name |
举例:
1 | java -jar /Users/crifan/dev/dev_tool/android/reverse_engineering/CFR/cfr-0.141.jar -jar com.huili.readingclub.jar --outputdir readingclub_CFR |
即可输出:
对应文件夹
包含:
- 所有的java源码
- summary.txt
- 记录了有哪些类转换失败和具体失败的原因
- 还是不错的,值得参考和利用,好知道具体哪些类转换期间出了啥问题
转载请注明:在路上 » 【已解决】用java反编译器CFR从jar包导出java源代码