折腾:
【未解决】nginx中配置了https的ssl证书后不起效果
期间,nginx配置了https,但是https页面始终拒绝访问。
感觉是防火墙和端口的问题。
但是去看了一堆netstat却又已经listen 443的端口了。
且去阿里云的安全组中也加了443端口允许外部访问。
但是通过:
去试试:iptables -L
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 | [root@xxx nginx]# iptables -LChain INPUT (policy ACCEPT)target prot opt source destination ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHEDACCEPT all -- anywhere anywhere INPUT_direct all -- anywhere anywhere INPUT_ZONES_SOURCE all -- anywhere anywhere INPUT_ZONES all -- anywhere anywhere DROP all -- anywhere anywhere ctstate INVALIDREJECT all -- anywhere anywhere reject-with icmp-host-prohibitedChain FORWARD (policy ACCEPT)target prot opt source destination ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHEDACCEPT all -- anywhere anywhere FORWARD_direct all -- anywhere anywhere FORWARD_IN_ZONES_SOURCE all -- anywhere anywhere FORWARD_IN_ZONES all -- anywhere anywhere FORWARD_OUT_ZONES_SOURCE all -- anywhere anywhere FORWARD_OUT_ZONES all -- anywhere anywhere DROP all -- anywhere anywhere ctstate INVALIDREJECT all -- anywhere anywhere reject-with icmp-host-prohibitedChain OUTPUT (policy ACCEPT)target prot opt source destination OUTPUT_direct all -- anywhere anywhere Chain FORWARD_IN_ZONES (1 references)target prot opt source destination FWDI_public all -- anywhere anywhere [goto] FWDI_public all -- anywhere anywhere [goto] Chain FORWARD_IN_ZONES_SOURCE (1 references)target prot opt source destination Chain FORWARD_OUT_ZONES (1 references)target prot opt source destination FWDO_public all -- anywhere anywhere [goto] FWDO_public all -- anywhere anywhere [goto] Chain FORWARD_OUT_ZONES_SOURCE (1 references)target prot opt source destination Chain FORWARD_direct (1 references)target prot opt source destination Chain FWDI_public (2 references)target prot opt source destination FWDI_public_log all -- anywhere anywhere FWDI_public_deny all -- anywhere anywhere FWDI_public_allow all -- anywhere anywhere ACCEPT icmp -- anywhere anywhere Chain FWDI_public_allow (1 references)target prot opt source destination Chain FWDI_public_deny (1 references)target prot opt source destination Chain FWDI_public_log (1 references)target prot opt source destination Chain FWDO_public (2 references)target prot opt source destination FWDO_public_log all -- anywhere anywhere FWDO_public_deny all -- anywhere anywhere FWDO_public_allow all -- anywhere anywhere Chain FWDO_public_allow (1 references)target prot opt source destination Chain FWDO_public_deny (1 references)target prot opt source destination Chain FWDO_public_log (1 references)target prot opt source destination Chain INPUT_ZONES (1 references)target prot opt source destination IN_public all -- anywhere anywhere [goto] IN_public all -- anywhere anywhere [goto] Chain INPUT_ZONES_SOURCE (1 references)target prot opt source destination Chain INPUT_direct (1 references)target prot opt source destination Chain IN_public (2 references)target prot opt source destination IN_public_log all -- anywhere anywhere IN_public_deny all -- anywhere anywhere IN_public_allow all -- anywhere anywhere ACCEPT icmp -- anywhere anywhere Chain IN_public_allow (1 references)target prot opt source destination ACCEPT tcp -- anywhere anywhere tcp dpt:ssh ctstate NEWACCEPT tcp -- anywhere anywhere tcp dpt:ftp-data ctstate NEWACCEPT tcp -- anywhere anywhere tcp dpt:ftp ctstate NEWACCEPT tcp -- anywhere anywhere tcp dpt:ssh ctstate NEWACCEPT tcp -- anywhere anywhere tcp dpt:http ctstate NEWACCEPT tcp -- anywhere anywhere tcp dpt:ddi-tcp-1 ctstate NEWACCEPT tcp -- anywhere anywhere tcp dpts:39000:safetynetp ctstate NEWChain IN_public_deny (1 references)target prot opt source destination Chain IN_public_log (1 references)target prot opt source destination Chain OUTPUT_direct (1 references)target prot opt source destination |
里面并没有看到https
难道阿里云安全组更改后,需要去重启服务器?
去重启试试
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 | [root@xxx nginx]# reboot -nowreboot: invalid option -- 'o'[root@xxx nginx]# reboot --nowreboot: unrecognized option '--now'[root@xxx nginx]# reboot --helpreboot [OPTIONS...] [ARG]Reboot the system. --help Show this help --halt Halt the machine -p --poweroff Switch off the machine --reboot Reboot the machine -f --force Force immediate halt/power-off/reboot -w --wtmp-only Don't halt/power-off/reboot, just write wtmp record -d --no-wtmp Don't write wtmp record --no-wall Don't send wall message before halt/power-off/reboot[root@xxx nginx]# reboot --reboot |
重启后:
1 | iptables -L |
输出结果和上面一样:
还是没有https
感觉是:
此服务器中实际上没有开启https的外部访问,所以要去:
当前CentOS中加上http的443端口,允许外部访问。
使得iptables -L能看到https
如何给CentOS的防火墙增加配置,支持https
使得iptables -L输出结果中允许https的TCP请求
nginx add https for iptables
nginx centos add https for iptables
好像是:
1 | iptables -A INPUT -p tcp --dport 443 -j ACCEPT |
1 | sudo iptables -I INPUT -p tcp -m tcp --dport 443 -j ACCEPT |
1 | * sudo iptables -I INPUT -p tcp -m tcp --dport 443 -j ACCEPT |
1 2 3 | [root@xxx nginx]# service iptables statusRedirecting to /bin/systemctl status iptables.serviceUnit iptables.service could not be found. |
此处没有iptables这个服务。
1 | iptables -A INPUT -m state --state NEW -p tcp --dport 443 -j ACCEPT |
1 | iptables -A INPUT -m state --state NEW -p tcp --dport 443 -j ACCEPT |
centos iptables add https
1 2 | * sudo iptables -A INPUT -p tcp --dport 443 -m conntrack --ctstate NEW,ESTABLISHED -j ACCEPT* sudo iptables -A OUTPUT -p tcp --sport 443 -m conntrack --ctstate ESTABLISHED -j ACCEPT |
1 2 | # Accept tcp packets on destination port 22 (SSH) iptables -A INPUT -p tcp --dport 22 -j ACCEPT |
好想操作完毕,还要去:
1 | service iptables save |
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 | [root@xxx nginx]# iptables --helpiptables v1.4.21Usage: iptables -[ACD] chain rule-specification [options] iptables -I chain [rulenum] rule-specification [options] iptables -R chain rulenum rule-specification [options] iptables -D chain rulenum [options] iptables -[LS] [chain [rulenum]] [options] iptables -[FZ] [chain] [options] iptables -[NX] chain iptables -E old-chain-name new-chain-name iptables -P chain target [options] iptables -h (print this help information)Commands:Either long or short options are allowed. --append -A chain Append to chain --check -C chain Check for the existence of a rule --delete -D chain Delete matching rule from chain --delete -D chain rulenum Delete rule rulenum (1 = first) from chain --insert -I chain [rulenum] Insert in chain as rulenum (default 1=first) --replace -R chain rulenum Replace rule rulenum (1 = first) in chain --list -L [chain [rulenum]] List the rules in a chain or all chains --list-rules -S [chain [rulenum]] Print the rules in a chain or all chains --flush -F [chain] Delete all rules in chain or all chains --zero -Z [chain [rulenum]] Zero counters in chain or all chains --new -N chain Create a new user-defined chain --delete-chain -X [chain] Delete a user-defined chain --policy -P chain target Change policy on chain to target --rename-chain -E old-chain new-chain Change chain name, (moving any references)Options: --ipv4 -4 Nothing (line is ignored by ip6tables-restore) --ipv6 -6 Error (line is ignored by iptables-restore)[!] --protocol -p proto protocol: by number or name, eg. `tcp'[!] --source -s address[/mask][...] source specification[!] --destination -d address[/mask][...] destination specification[!] --in-interface -i input name[+] network interface name ([+] for wildcard) --jump -j target target for rule (may load target extension) --goto -g chain jump to chain with no return --match -m match extended match (may load extension) --numeric -n numeric output of addresses and ports[!] --out-interface -o output name[+] network interface name ([+] for wildcard) --table -t table table to manipulate (default: `filter') --verbose -v verbose mode --wait -w [seconds] maximum wait to acquire xtables lock before give up --wait-interval -W [usecs] wait time to try to acquire xtables lock default is 1 second --line-numbers print line numbers when listing --exact -x expand numbers (display exact values)[!] --fragment -f match second or further fragments only --modprobe=<command> try to insert modules using this command --set-counters PKTS BYTES set the counter during insert/append[!] --version -V print package version. |
然后试试:
1 | iptables -A INPUT -p tcp --dport 443 -j ACCEPT |
然后输出结果变了:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 | [root@xxx nginx]# iptables -LChain INPUT (policy ACCEPT)target prot opt source destination ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHEDACCEPT all -- anywhere anywhere INPUT_direct all -- anywhere anywhere INPUT_ZONES_SOURCE all -- anywhere anywhere INPUT_ZONES all -- anywhere anywhere DROP all -- anywhere anywhere ctstate INVALIDREJECT all -- anywhere anywhere reject-with icmp-host-prohibitedACCEPT tcp -- anywhere anywhere tcp dpt:https...Chain IN_public_allow (1 references)target prot opt source destination ACCEPT tcp -- anywhere anywhere tcp dpt:ssh ctstate NEWACCEPT tcp -- anywhere anywhere tcp dpt:ftp-data ctstate NEWACCEPT tcp -- anywhere anywhere tcp dpt:ftp ctstate NEWACCEPT tcp -- anywhere anywhere tcp dpt:ssh ctstate NEWACCEPT tcp -- anywhere anywhere tcp dpt:http ctstate NEWACCEPT tcp -- anywhere anywhere tcp dpt:ddi-tcp-1 ctstate NEWACCEPT tcp -- anywhere anywhere tcp dpts:39000:safetynetp ctstate NEWChain IN_public_deny (1 references)target prot opt source destination ... |
但是只是:
Chain INPUT (policy ACCEPT)
部分多了:
ACCEPT tcp — anywhere anywhere tcp dpt:https
原以为的:
Chain IN_public_allow (1 references)
没有变化
先不管,去:
1 2 | [root@xxx nginx]# service iptables saveThe service command supports only basic LSB actions (start, stop, restart, try-restart, reload, force-reload, status). For other actions, please try to use systemctl. |
无法保存。
重启服务器,看看
iptables -L
是否保存了新增的规则
结果并没有:
1 2 3 4 5 6 7 8 9 10 11 | [root@xxx nginx]# iptables -LChain INPUT (policy ACCEPT)target prot opt source destination ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHEDACCEPT all -- anywhere anywhere INPUT_direct all -- anywhere anywhere INPUT_ZONES_SOURCE all -- anywhere anywhere INPUT_ZONES all -- anywhere anywhere DROP all -- anywhere anywhere ctstate INVALIDREJECT all -- anywhere anywhere reject-with icmp-host-prohibited... |
继续参考:
去用-I insert去插入到:
1 2 3 4 5 6 7 8 9 10 11 12 | [root@xxx nginx]# iptables -L --line-numbers...Chain IN_public_allow (1 references)num target prot opt source destination 1 ACCEPT tcp -- anywhere anywhere tcp dpt:ssh ctstate NEW2 ACCEPT tcp -- anywhere anywhere tcp dpt:ftp-data ctstate NEW3 ACCEPT tcp -- anywhere anywhere tcp dpt:ftp ctstate NEW4 ACCEPT tcp -- anywhere anywhere tcp dpt:ssh ctstate NEW5 ACCEPT tcp -- anywhere anywhere tcp dpt:http ctstate NEW6 ACCEPT tcp -- anywhere anywhere tcp dpt:ddi-tcp-1 ctstate NEW7 ACCEPT tcp -- anywhere anywhere tcp dpts:39000:safetynetp ctstate NEW... |
中的dpt:http上面
但是虽然知道是:
1 | iptables -I IN_public_allow 5 -p tcp --dport 443 -j ACCEPT |
但还是不会保存。
centos 7 iptables 添加https
先去安装:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 | [root@xxx nginx]# service iptables statusRedirecting to /bin/systemctl status iptables.serviceUnit iptables.service could not be found.[root@xxx nginx]# yum install -y iptablesLoaded plugins: fastestmirrorbase | 3.6 kB 00:00:00 epel | 3.2 kB 00:00:00 extras | 3.4 kB 00:00:00 updates | 3.4 kB 00:00:00 (1/7): base/7/x86_64/group_gz | 166 kB 00:00:00 (2/7): epel/x86_64/group_gz | 88 kB 00:00:00 (3/7): epel/x86_64/updateinfo | 932 kB 00:00:00 (4/7): extras/7/x86_64/primary_db | 205 kB 00:00:00 (5/7): epel/x86_64/primary | 3.6 MB 00:00:00 (6/7): updates/7/x86_64/primary_db | 6.0 MB 00:00:00 (7/7): base/7/x86_64/primary_db | 5.9 MB 00:00:00 Determining fastest mirrorsepel 12719/12719Resolving Dependencies--> Running transaction check---> Package iptables.x86_64 0:1.4.21-18.2.el7_4 will be updated---> Package iptables.x86_64 0:1.4.21-24.1.el7_5 will be an update--> Finished Dependency ResolutionDependencies Resolved========================================================================================================================================================================================= Package Arch Version Repository Size=========================================================================================================================================================================================Updating: iptables x86_64 1.4.21-24.1.el7_5 updates 432 kTransaction Summary=========================================================================================================================================================================================Upgrade 1 PackageTotal download size: 432 kDownloading packages:Delta RPMs disabled because /usr/bin/applydeltarpm not installed.iptables-1.4.21-24.1.el7_5.x86_64.rpm | 432 kB 00:00:00 Running transaction checkRunning transaction testTransaction test succeededRunning transaction Updating : iptables-1.4.21-24.1.el7_5.x86_64 1/2 Cleanup : iptables-1.4.21-18.2.el7_4.x86_64 2/2 Verifying : iptables-1.4.21-24.1.el7_5.x86_64 1/2 Verifying : iptables-1.4.21-18.2.el7_4.x86_64 2/2 Updated: iptables.x86_64 0:1.4.21-24.1.el7_5 Complete![root@xxx nginx]# yum update iptables Loaded plugins: fastestmirrorLoading mirror speeds from cached hostfileNo packages marked for update[root@xxx nginx]# yum install iptables-servicesLoaded plugins: fastestmirrorLoading mirror speeds from cached hostfileResolving Dependencies--> Running transaction check---> Package iptables-services.x86_64 0:1.4.21-24.1.el7_5 will be installed--> Finished Dependency ResolutionDependencies Resolved========================================================================================================================================================================================= Package Arch Version Repository Size=========================================================================================================================================================================================Installing: iptables-services x86_64 1.4.21-24.1.el7_5 updates 51 kTransaction Summary=========================================================================================================================================================================================Install 1 PackageTotal download size: 51 kInstalled size: 25 kIs this ok [y/d/N]: yDownloading packages:iptables-services-1.4.21-24.1.el7_5.x86_64.rpm | 51 kB 00:00:00 Running transaction checkRunning transaction testTransaction test succeededRunning transaction Installing : iptables-services-1.4.21-24.1.el7_5.x86_64 1/1 Verifying : iptables-services-1.4.21-24.1.el7_5.x86_64 1/1 Installed: iptables-services.x86_64 0:1.4.21-24.1.el7_5 Complete! |
【已解决】CentOS 7中如何通过firewalld去添加https的443端口
此处故意用firewalld去删除之前添加的https的规则
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 | [root@xxx nginx]# firewall-cmd --zone=public --remove-service=https --permanentsuccess[root@xxx nginx]# firewall-cmd --zone=public --list-allpublic (active) target: default icmp-block-inversion: no interfaces: eth0 sources: services: ssh dhcpv6-client https ports: 20/tcp 21/tcp 22/tcp 80/tcp 8888/tcp 39000-40000/tcp 443/tcp protocols: masquerade: no forward-ports: source-ports: icmp-blocks: rich rules: |
发现忘了reload,再去:
1 2 | [root@xxx nginx]# firewall-cmd --reloadsuccess |
结果以为:iptables中没了443,结果还有:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 | [root@xxx nginx]# iptables -L -nChain INPUT (policy ACCEPT)target prot opt source destination ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHEDACCEPT all -- 0.0.0.0/0 0.0.0.0/0 INPUT_direct all -- 0.0.0.0/0 0.0.0.0/0 INPUT_ZONES_SOURCE all -- 0.0.0.0/0 0.0.0.0/0 INPUT_ZONES all -- 0.0.0.0/0 0.0.0.0/0 DROP all -- 0.0.0.0/0 0.0.0.0/0 ctstate INVALIDREJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibitedChain FORWARD (policy ACCEPT)target prot opt source destination ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHEDACCEPT all -- 0.0.0.0/0 0.0.0.0/0 FORWARD_direct all -- 0.0.0.0/0 0.0.0.0/0 FORWARD_IN_ZONES_SOURCE all -- 0.0.0.0/0 0.0.0.0/0 FORWARD_IN_ZONES all -- 0.0.0.0/0 0.0.0.0/0 FORWARD_OUT_ZONES_SOURCE all -- 0.0.0.0/0 0.0.0.0/0 FORWARD_OUT_ZONES all -- 0.0.0.0/0 0.0.0.0/0 DROP all -- 0.0.0.0/0 0.0.0.0/0 ctstate INVALIDREJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibitedChain OUTPUT (policy ACCEPT)target prot opt source destination OUTPUT_direct all -- 0.0.0.0/0 0.0.0.0/0 Chain FORWARD_IN_ZONES (1 references)target prot opt source destination FWDI_public all -- 0.0.0.0/0 0.0.0.0/0 [goto] FWDI_public all -- 0.0.0.0/0 0.0.0.0/0 [goto] Chain FORWARD_IN_ZONES_SOURCE (1 references)target prot opt source destination Chain FORWARD_OUT_ZONES (1 references)target prot opt source destination FWDO_public all -- 0.0.0.0/0 0.0.0.0/0 [goto] FWDO_public all -- 0.0.0.0/0 0.0.0.0/0 [goto] Chain FORWARD_OUT_ZONES_SOURCE (1 references)target prot opt source destination Chain FORWARD_direct (1 references)target prot opt source destination Chain FWDI_public (2 references)target prot opt source destination FWDI_public_log all -- 0.0.0.0/0 0.0.0.0/0 FWDI_public_deny all -- 0.0.0.0/0 0.0.0.0/0 FWDI_public_allow all -- 0.0.0.0/0 0.0.0.0/0 ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0 Chain FWDI_public_allow (1 references)target prot opt source destination Chain FWDI_public_deny (1 references)target prot opt source destination Chain FWDI_public_log (1 references)target prot opt source destination Chain FWDO_public (2 references)target prot opt source destination FWDO_public_log all -- 0.0.0.0/0 0.0.0.0/0 FWDO_public_deny all -- 0.0.0.0/0 0.0.0.0/0 FWDO_public_allow all -- 0.0.0.0/0 0.0.0.0/0 Chain FWDO_public_allow (1 references)target prot opt source destination Chain FWDO_public_deny (1 references)target prot opt source destination Chain FWDO_public_log (1 references)target prot opt source destination Chain INPUT_ZONES (1 references)target prot opt source destination IN_public all -- 0.0.0.0/0 0.0.0.0/0 [goto] IN_public all -- 0.0.0.0/0 0.0.0.0/0 [goto] Chain INPUT_ZONES_SOURCE (1 references)target prot opt source destination Chain INPUT_direct (1 references)target prot opt source destination Chain IN_public (2 references)target prot opt source destination IN_public_log all -- 0.0.0.0/0 0.0.0.0/0 IN_public_deny all -- 0.0.0.0/0 0.0.0.0/0 IN_public_allow all -- 0.0.0.0/0 0.0.0.0/0 ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0 Chain IN_public_allow (1 references)target prot opt source destination ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22 ctstate NEWACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:443 ctstate NEWACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:20 ctstate NEWACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:21 ctstate NEWACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22 ctstate NEWACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:80 ctstate NEWACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:8888 ctstate NEWACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpts:39000:40000 ctstate NEWACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:443 ctstate NEWChain IN_public_deny (1 references)target prot opt source destination Chain IN_public_log (1 references)target prot opt source destination Chain OUTPUT_direct (1 references)target prot opt source destination |
的
Chain IN_public_allow (1 references)
中还是有https的。
再去重启reboot –reboot
结果iptables中还是有443
再去试试:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 | [root@xxx ~]# firewall-cmd --zone=public --remove-service=https --permanentWarning: NOT_ENABLED: httpssuccess[root@xxx ~]# firewall-cmd --zone=public --remove-port=443/tcp --permanent success[root@xxx ~]# firewall-cmd --zone=public --list-allpublic (active) target: default icmp-block-inversion: no interfaces: eth0 sources: services: ssh dhcpv6-client ports: 20/tcp 21/tcp 22/tcp 80/tcp 8888/tcp 39000-40000/tcp 443/tcp protocols: masquerade: no forward-ports: source-ports: icmp-blocks: rich rules: [root@xxx ~]# firewall-cmd --reload success[root@xxx ~]# firewall-cmd --zone=public --list-allpublic (active) target: default icmp-block-inversion: no interfaces: eth0 sources: services: ssh dhcpv6-client ports: 20/tcp 21/tcp 22/tcp 80/tcp 8888/tcp 39000-40000/tcp protocols: masquerade: no forward-ports: source-ports: icmp-blocks: rich rules: |
然后再去看看:
iptables -L -n
结果:
1 2 3 4 5 6 7 8 9 | Chain IN_public_allow (1 references)target prot opt source destination ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22 ctstate NEWACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:20 ctstate NEWACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:21 ctstate NEWACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22 ctstate NEWACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:80 ctstate NEWACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:8888 ctstate NEWACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpts:39000:40000 ctstate NEW |
中的确没有了https的443了。
访问:
立刻出现拒绝:
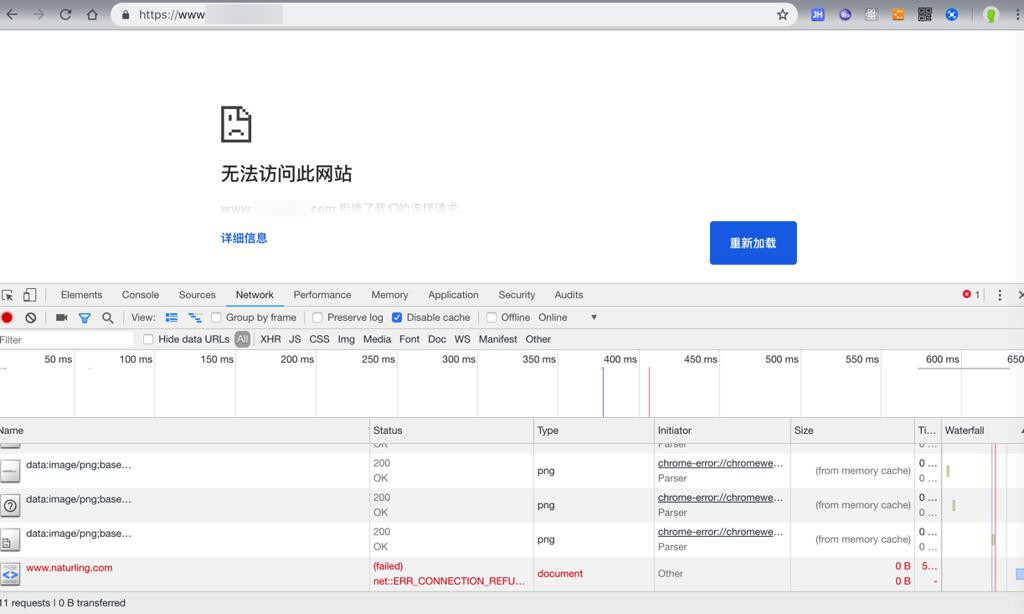
然后再去尝试用iptables去添加https的443的tcp:
1 2 3 | [root@xxx ~]# iptables -I IN_public_allow 5 -p tcp --dport 443 -j ACCEPT[root@xxx ~]# service iptables saveiptables: Saving firewall rules to /etc/sysconfig/iptables:[ OK ] |
看来是添加进去了。
去看看效果:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 | [root@xxx ~]# iptables -L --line-numbers Chain INPUT (policy ACCEPT)num target prot opt source destination 1 ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED2 ACCEPT all -- anywhere anywhere 3 INPUT_direct all -- anywhere anywhere 4 INPUT_ZONES_SOURCE all -- anywhere anywhere 5 INPUT_ZONES all -- anywhere anywhere 6 DROP all -- anywhere anywhere ctstate INVALID7 REJECT all -- anywhere anywhere reject-with icmp-host-prohibitedChain FORWARD (policy ACCEPT)num target prot opt source destination 1 ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED2 ACCEPT all -- anywhere anywhere 3 FORWARD_direct all -- anywhere anywhere 4 FORWARD_IN_ZONES_SOURCE all -- anywhere anywhere 5 FORWARD_IN_ZONES all -- anywhere anywhere 6 FORWARD_OUT_ZONES_SOURCE all -- anywhere anywhere 7 FORWARD_OUT_ZONES all -- anywhere anywhere 8 DROP all -- anywhere anywhere ctstate INVALID9 REJECT all -- anywhere anywhere reject-with icmp-host-prohibitedChain OUTPUT (policy ACCEPT)num target prot opt source destination 1 OUTPUT_direct all -- anywhere anywhere Chain FORWARD_IN_ZONES (1 references)num target prot opt source destination 1 FWDI_public all -- anywhere anywhere [goto] 2 FWDI_public all -- anywhere anywhere [goto] Chain FORWARD_IN_ZONES_SOURCE (1 references)num target prot opt source destination Chain FORWARD_OUT_ZONES (1 references)num target prot opt source destination 1 FWDO_public all -- anywhere anywhere [goto] 2 FWDO_public all -- anywhere anywhere [goto] Chain FORWARD_OUT_ZONES_SOURCE (1 references)num target prot opt source destination Chain FORWARD_direct (1 references)num target prot opt source destination Chain FWDI_public (2 references)num target prot opt source destination 1 FWDI_public_log all -- anywhere anywhere 2 FWDI_public_deny all -- anywhere anywhere 3 FWDI_public_allow all -- anywhere anywhere 4 ACCEPT icmp -- anywhere anywhere Chain FWDI_public_allow (1 references)num target prot opt source destination Chain FWDI_public_deny (1 references)num target prot opt source destination Chain FWDI_public_log (1 references)num target prot opt source destination Chain FWDO_public (2 references)num target prot opt source destination 1 FWDO_public_log all -- anywhere anywhere 2 FWDO_public_deny all -- anywhere anywhere 3 FWDO_public_allow all -- anywhere anywhere Chain FWDO_public_allow (1 references)num target prot opt source destination Chain FWDO_public_deny (1 references)num target prot opt source destination Chain FWDO_public_log (1 references)num target prot opt source destination Chain INPUT_ZONES (1 references)num target prot opt source destination 1 IN_public all -- anywhere anywhere [goto] 2 IN_public all -- anywhere anywhere [goto] Chain INPUT_ZONES_SOURCE (1 references)num target prot opt source destination Chain INPUT_direct (1 references)num target prot opt source destination Chain IN_public (2 references)num target prot opt source destination 1 IN_public_log all -- anywhere anywhere 2 IN_public_deny all -- anywhere anywhere 3 IN_public_allow all -- anywhere anywhere 4 ACCEPT icmp -- anywhere anywhere Chain IN_public_allow (1 references)num target prot opt source destination 1 ACCEPT tcp -- anywhere anywhere tcp dpt:ssh ctstate NEW2 ACCEPT tcp -- anywhere anywhere tcp dpt:ftp-data ctstate NEW3 ACCEPT tcp -- anywhere anywhere tcp dpt:ftp ctstate NEW4 ACCEPT tcp -- anywhere anywhere tcp dpt:ssh ctstate NEW5 ACCEPT tcp -- anywhere anywhere tcp dpt:https6 ACCEPT tcp -- anywhere anywhere tcp dpt:http ctstate NEW7 ACCEPT tcp -- anywhere anywhere tcp dpt:ddi-tcp-1 ctstate NEW8 ACCEPT tcp -- anywhere anywhere tcp dpts:39000:safetynetp ctstate NEWChain IN_public_deny (1 references)num target prot opt source destination Chain IN_public_log (1 references)num target prot opt source destination Chain OUTPUT_direct (1 references)num target prot opt source destination |
可见:
Chain IN_public_allow (1 references)
部分,新增了:
5 ACCEPT tcp — anywhere anywhere tcp dpt:https
虽然和之前的配置,比如:
6 ACCEPT tcp — anywhere anywhere tcp dpt:http ctstate NEW
有点点不一样:
是可以打开的了。
不过用刚才:
【已解决】CentOS 7中如何通过firewalld去添加https的443端口
中的:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 | [root@xxx ~]# firewall-cmd --query-service httpsno[root@xxx ~]# firewall-cmd --zone=public --list-allpublic (active) target: default icmp-block-inversion: no interfaces: eth0 sources: services: ssh dhcpv6-client ports: 20/tcp 21/tcp 22/tcp 80/tcp 8888/tcp 39000-40000/tcp protocols: masquerade: no forward-ports: source-ports: icmp-blocks: rich rules: |
发现还是不支持的。
看来上面是少了:
-m state –state NEW
的参数了。
去删除掉刚才加的https:
1 2 3 4 5 6 7 8 9 10 11 12 13 | [root@xxx ~]# iptables -D IN_public_allow 5[root@xxx ~]# iptables -L --line-numbers ...Chain IN_public_allow (1 references)num target prot opt source destination 1 ACCEPT tcp -- anywhere anywhere tcp dpt:ssh ctstate NEW2 ACCEPT tcp -- anywhere anywhere tcp dpt:ftp-data ctstate NEW3 ACCEPT tcp -- anywhere anywhere tcp dpt:ftp ctstate NEW4 ACCEPT tcp -- anywhere anywhere tcp dpt:ssh ctstate NEW5 ACCEPT tcp -- anywhere anywhere tcp dpt:http ctstate NEW6 ACCEPT tcp -- anywhere anywhere tcp dpt:ddi-tcp-1 ctstate NEW7 ACCEPT tcp -- anywhere anywhere tcp dpts:39000:safetynetp ctstate NEW... |
不要忘了:
1 2 | [root@xxx ~]# service iptables saveiptables: Saving firewall rules to /etc/sysconfig/iptables:[ OK ] |
再去添加:
1 | iptables -I IN_public_allow 5 -m state --state NEW -p tcp --dport 443 -j ACCEPT |
结果输出的顺序不一致:
1 2 3 4 5 6 7 8 9 10 | Chain IN_public_allow (1 references)num target prot opt source destination 1 ACCEPT tcp -- anywhere anywhere tcp dpt:ssh ctstate NEW2 ACCEPT tcp -- anywhere anywhere tcp dpt:ftp-data ctstate NEW3 ACCEPT tcp -- anywhere anywhere tcp dpt:ftp ctstate NEW4 ACCEPT tcp -- anywhere anywhere tcp dpt:ssh ctstate NEW5 ACCEPT tcp -- anywhere anywhere state NEW tcp dpt:https6 ACCEPT tcp -- anywhere anywhere tcp dpt:http ctstate NEW7 ACCEPT tcp -- anywhere anywhere tcp dpt:ddi-tcp-1 ctstate NEW8 ACCEPT tcp -- anywhere anywhere tcp dpts:39000:safetynetp ctstate NEW |
所以再去删了,重新添加:
1 | iptables -I IN_public_allow 5 -p tcp -m state --state NEW --dport 443 -j ACCEPT |
结果现象一样,还是:
1 | state NEW tcp dpt:https |
而不是以为的:
1 | tcp dpt:https state NEW |
不过不论是:
1 2 | state NEW tcp dpt:httpstcp dpt:https |
都是可以work-》https地址都可以打开的。
不过呢,貌似和firewalld不兼容,查出来都不支持https:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 | [root@xxx ~]# firewall-cmd --query-service httpsno[root@xxx ~]# firewall-cmd --zone=public --list-allpublic (active) target: default icmp-block-inversion: no interfaces: eth0 sources: services: ssh dhcpv6-client ports: 20/tcp 21/tcp 22/tcp 80/tcp 8888/tcp 39000-40000/tcp protocols: masquerade: no forward-ports: source-ports: icmp-blocks: rich rules: |
都没有443。
不过也无所谓了。
【总结】
此处CentOS中用iptables管理端口权限:
如果用:
1 | service iptables save |
出错:
1 | The service command supports only basic LSB actions (start, stop, restart, try-restart, reload, force-reload, status). For other actions, please try to use systemctl. |
或:
1 | service iptables status |
出错:
1 2 | Redirecting to /bin/systemctl status iptables.serviceUnit iptables.service could not be found. |
说明:iptables管理工具没有安装,需要去安装:
1 2 3 | yum install -y iptablesyum update iptables yum install -y iptables-services |
然后再去管理。
由于用CentOS 7中默认用firewalld去管理端口的,所以为了防止iptables和firewalld冲突,所以按道理,应该去根据:
说的,先去“禁用/停止自带的firewalld服务”
1 2 3 4 | #停止firewalld服务systemctl stop firewalld#禁用firewalld服务systemctl mask firewalld |
不过,此处没有。后续也可以操作,成功添加https的443端口的。
不过,由于后来发现:firewalld比iptables好用太多,所有后续还是建议用firewalld去管理端口。
详见:
【已解决】CentOS 7中如何通过firewalld去添加https的443端口
此处单独说:
用iptables添加https的443端口的话,则是:
此处打算是用I= Insert,而不是很多人常说的A=Add,所以先要搞清楚插入的位置。
先用:
1 | iptables -L --line-numbers |
去看到:
1 2 3 4 5 6 7 8 9 | Chain IN_public_allow (1 references)num target prot opt source destination 1 ACCEPT tcp -- anywhere anywhere tcp dpt:ssh ctstate NEW2 ACCEPT tcp -- anywhere anywhere tcp dpt:ftp-data ctstate NEW3 ACCEPT tcp -- anywhere anywhere tcp dpt:ftp ctstate NEW4 ACCEPT tcp -- anywhere anywhere tcp dpt:ssh ctstate NEW5 ACCEPT tcp -- anywhere anywhere tcp dpt:http ctstate NEW6 ACCEPT tcp -- anywhere anywhere tcp dpt:ddi-tcp-1 ctstate NEW7 ACCEPT tcp -- anywhere anywhere tcp dpts:39000:safetynetp ctstate NEW |
想要插入在http之前,http的num是5,所以用:
1 | iptables -I IN_public_allow 5 -p tcp --dport 443 -j ACCEPT |
表示:
- I: Insert插入到
- IN_public_allow:对应的区域zone,chain链
- 5:num是5,对应着上面的
- 5 ACCEPT tcp — anywhere anywhere tcp dpt:http ctstate NEW
- -p tcp:protocol协议是tcp
- –dport 443:端口是433
- -j ACCEPT:target是ACCEPT接受
- 即允许这条规则
- 其中:
- –jump -j target
- target for rule (may load target extension)
然后通过:
1 | iptables -L --line-numbers |
可以看到最新添加的https:
1 2 3 4 5 6 | Chain IN_public_allow (1 references)num target prot opt source destination ...5 ACCEPT tcp -- anywhere anywhere tcp dpt:https6 ACCEPT tcp -- anywhere anywhere tcp dpt:http ctstate NEW... |
然后记得不要忘了:
1 | service iptables save |
去保存最新的配置。
此时443的https请求就可以正常传入了 -》 就可以正常去打开https的地址了。
其中:
如果换用:
1 | iptables -I IN_public_allow 5 -m state --state NEW -p tcp --dport 443 -j ACCEPT |
输出的则是:
1 | state NEW tcp dpt:https |
以及:
即使换用:
1 | iptables -I IN_public_allow 5 -p tcp -m state --state NEW --dport 443 -j ACCEPT |
也还是输出:
1 | state NEW tcp dpt:https |
而不是以为的(和别的http等保持一致的)
1 | tcp dpt:http ctstate NEW |
另外:
想要去删除刚插入的那条https记录,则可以:
1 | iptables -D IN_public_allow 5 |
其中的5是通过:
iptables -L –line-numbers
最新的https的那条的num
另外注意:
此处iptables的结果和firewalld不兼容,所以:
1 | firewall-cmd --query-service https |
输出是:no
以及:
1 | firewall-cmd --zone=public --list-all |
看到的是:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 | [root@xxx ~]# firewall-cmd --zone=public --list-allpublic (active) target: default icmp-block-inversion: no interfaces: eth0 sources: services: ssh dhcpv6-client ports: 20/tcp 21/tcp 22/tcp 80/tcp 8888/tcp 39000-40000/tcp protocols: masquerade: no forward-ports: source-ports: icmp-blocks: rich rules: |
也是没有支持https的。