折腾:
期间,去调试抓包时,对于:
看到的api请求:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 | http://www.xiaohuasheng.cn:83/Reading.svc/selfReadingBookQuery2 POST /Reading.svc/selfReadingBookQuery2 HTTP/1.1Content-Type application/jsonAuthorization NSTp9~)NwSfrXp@\userId 1134723timestamp 1552528881signature fabb3bf23d198ddfbebd14e0d72baaecContent-Length 176Host www.xiaohuasheng.cn:83User-Agent Mozilla/5.0 (Linux; U; Android 4.4.2; zh-cn; A0001 Build/KOT49H) AppleWebKit/533.1 (KHTML, like Gecko) Version/4.0 Mobile Safari/533.1Cookie ASP.NET_SessionId=xdmahehpqguzinkktogltluaCookie2 $Version=1Accept-Encoding gzipConnection keep-alive |
所返回的数据都是统一格式:
1 2 3 4 5 6 | { "C": 2, "J": "H4sIAAAAAAAEALVXW0\/bSBj9K1Z........9n\/Q8\/u0\/UDEtQFAPAAA=", "M": "1001", "ST": null} |
此处完整的值是:
1 2 3 4 5 6 | { "C": 2, "J": "H4sIAAAAAAAEALVXW0\/bSBj9K1Ze9oVdYjtOnD6WbbdoL0SlfVrtg5tMg7eJjWynW7SqFFbcuqQQSrmkgdJCubRLCiy3XEHqT6k8Y+epf2E\/xyFXmy2VKkWRx554vjlnzjlffv3TM\/zAc43zMj2e8JAoIRXdEbUY8lzz4NIirrwlq7Pm9IG5l8PpPfNZRi9s4acLnh4PkqIxUR26mAx37iuypPXJD5EC48ERVUPx3hv2rEGkiEgNiWEtoaBexkvzNM0wtJflaT8fDHz3+3AUXnBPlh\/0yQlJ81yjmWCPRxOiKrwK1iZja3itgMdL1IdTyigtk5Xd6vK4uVcb24WZ798Ya5u158\/XyFGJTKWrC+fN+dZVdfWlmXlBXo5ZA\/sKllUT8bigjPRLAxIaRJKGpLC1o4\/JFeP5Dll5gjf2rV2nd\/FksQ7F39mPyVXrp3IsMpCw6n3cYwPJ0t04ju8bmRKemjCK23bV3fANamiY6pc0mbqNhIgoRTvxrAP5E3qIYjcbDwaUfklCSkiIot5AsBfvj1ZX1x3Q9AZ6PEIiIsr1GyzrbcDbWpiFSwhKS4gSdVuQInKcuiUnVFSDuTYPJrmDaV0BYNW1w+r6XO03s3vGXwV7x3FRCimiBS3L8zAUHtWHviCcPVkRo40JPON1pcU4m8HZip4vkePRRknGk7eeCwY4OthNQfqILMwCEV\/nKLPwzfiZAO\/zOR1l+suP8vYczm01n1\/1aDcxZyxBNTGvDdsw93H8ZVIwJ98ZYydQNixug2hXVZdCA3yLuQ7wycE72LExW\/maPuLz+gN0N\/gM4\/188DuE8H++0imIJhkO+NNM25mnLQm04c8EuMvwt8vGubc4lzZejAGUZHHSTB6SleNW\/IMO9pM9A7CrWxPGIZjQUjfkd4YQdVe9JysSunAfKqTIUUWIx9HVfYhnfa5GxLGutnNRQShxz1rAKsIBYwefabcWv78VZtYCtQ1mmgv6XXEmy\/OwFJwTcyeJn6X08rKxnSQL43pxGjC3nGcrY5TmcXqqAThr8dqBONBFpub08gt4mV6cAH7M41OS24Sd6IXp6mYZF\/41ph2Y6Kf6BKnGAfXzCHVTVFSNqiFNXRfVcELUrs4GwzPuscC3p4I1dmHnlqAMI6VPjsVESf18Ytqg93vdXR2\/P8GLoK1TkpmvQ52ttNr7p3JKLxbhAlfWzYPXthDwm21j6sA5h30OQqhYy6zsG+kJvD+Hx84vz+RfBE2UJSFG\/YAsMQwPiWHqRzGi1ghCinp1MmiGcyUjyLmC35kCToXdiCTCtduXRnV7JNBcq1Y4plMrftpdKnizUh1dIhNnQIx12Eu7eH+WLJ3gZEbPPyXZMzgGZKUIIiAzm+b2lnmeIa9OgVrwok\/l0YZ+fBzXRZTxJEuONu39kldzeGq1unzSzc\/Ao\/uyEmlY1h0Fobpa6G\/Zy3OkgyM7SbwsDWkCHWmA5xzEEmyqww5DMl12SY56ZXclEV6uitoI+ClSHXXj3CHRbFta82yXjfkD7mICunE+j2eXyO66eT5jx0Ujsc3zLMCJx3fIYoG8bjqZL9Ad3ZbAUv+0bg8XypZwsrluPi7c4boYBR\/TgJgwGraO5NWF4qdddcJ3mBbvblr2Fajd3N6wxhcFfp5W2l2tmhmzXa3v+\/oQvAQaAZKaxHvl9gwKtpHnYzqjng5aHa+bsMZ37KAGzizHym2RV6\/tdreuiIUMWU03afN2BxAwRHKp6tox9Ajk6CV8QHUOhMUEVQXvuA7oqtQfojYE3X4MdRmbg3ZaAqYmHToA3ywDbbDTnzn+ixvgviExFvlGpUIxYcSpx6pxUdunu5iY9r8bTFfrxQUu8bn9CWNjx2609PyMjaZ5soHnDvXKfPVdCpoBvZjS80U9n\/Q8\/u0\/UDEtQFAPAAA=", "M": "1001", "ST": null} |
明显J都是加了密的数据:
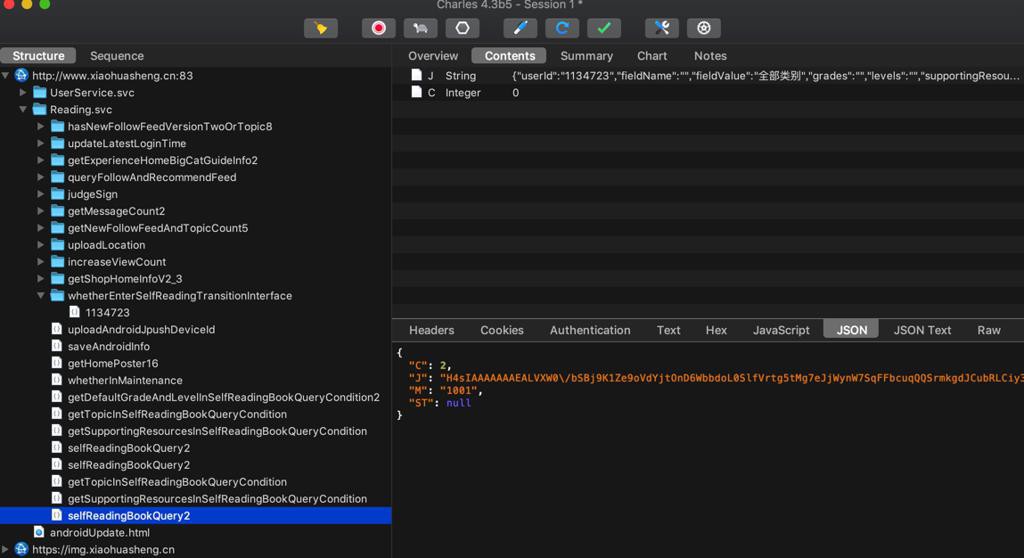
之前很多api请求也是类似的数据:
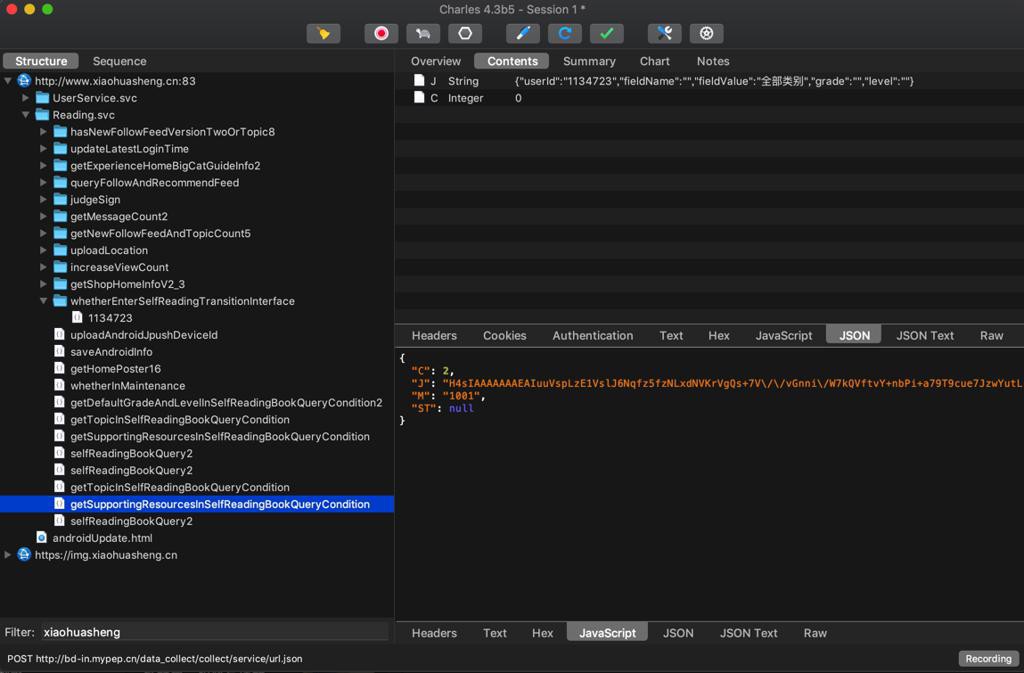
现在需要的是:
想办法看看如何破解,解密出J字段的原始文字
C J M ST
http response C J M ST
xiaohuasheng C J M ST
xiaohuasheng J json
xiaohuasheng H4sIAAAAA
xiaohuasheng H4sI
xiaohuasheng rest api J
xiaohuasheng app encrpy
感觉只能是:
反编译安卓的apk,找到源码,或许可能,还未必,能找到解密的算法,才能得到原始文字
xiaohuasheng app 加密
xiaohuasheng app 加密 J
xiaohuasheng app 加密 CJM
android app 加密 CJM
android http api CJM
android http api C J M ST
android api json C J M ST
C J M ST
c j m st encryption
c j m st json
selfReadingBookQuery2
Reading.svc
rest api json encrypt
用了某种加密算法
“Encrypted field from the REST response JSON (description form field):
“description”:”84d1d37bdb7a3200750573ffbf96191f:0aZdRxsIqSpFtuszNr73na/J9JuMLNB0J6T2f2FrV0sUlMmbW4prbZMmXGnLU4W6CDlb5F1lb8js\r\nRHw6tfyZd5ZL//ZUlozE916wvP+zd+uUfjpk2Bl9o2uAu+1bsNoAVdtP5m5fbnkjxf9yLRzREVVO\r\nIwYQOxNI/CeX2dzF/Uc=”
Encryption method: AES 128 Bit.
Password: 1234567890123456
Original Text: “new description for new incident.。。。”
感觉此处像是,某种加密算法,类似这里的AES 128 Bit
很明显,网上没有这种算法,因为不知道是什么算法。而猜,是没用的。
后来是去继续研究:
【已解决】尝试破解小花生app安卓apk希望看到api返回的json中的J的解密算法得到明文
期间,通过:
【已解决】从不同版本的小花生apk中反编译出包含业务逻辑代码的dex和jar包源码
以及:
【已解决】从反编译小花生apk得到的包含业务逻辑代码中找到J字段解码的逻辑并用Python实现
而解决的。