折腾:
【已解决】Charles抓包分析某app中如何获取mp4视频地址
期间,现在是:
部分https包,可以用Charles解密查看明文
部分https包,Charles无法看到明文,要么是加密的乱码,要么是红色unknown错误
部分https的请求,Charles无法解析 解密 为明文
注:
后来已经确定是:
即使你正确安装了Charles的SSL证书(不论是电脑端还是手机端),结果安卓app中,部分的https的包,还是加密的,无法看到明文,其实现方式就是:
- ssl pinning
- =Certificate pinning
- =cert pinning
- = ssl Certificate pinning
- =SSL certificate checking
- =ssl证书探测
- =ssl证书检测
所以接下来就是如何解决ssl pinning的问题了:
charles https partial not parse
Version 4.1.4
* Mirror tool now supprts partial responses (so you can mirror some streaming video)
Version 4.2.6
* HTTP 2 handling faults corrected
* Date parsing fixed from Charles on iOS when used in London
此处已经是最新的4.2.6了
charles https sometime not parse
关于SSL默认全部没有开启,主要考虑是:
万一有银行账户之类的信息,万一全部开启解密,就能看到密码明文了,就不安全了。
所以默认不开启,只有你在SSL的过滤列表中加上,才开启:
-》
-》
“SSL Pinning
Note that some apps implement SSL certificate pinning which means they specifically validate the root certificate. Because the app is itself verifying the root certificate it will not accept Charles’s certificate and will fail the connection. If you have successfully installed the Charles root SSL certificate and can browse SSL websites using SSL Proxying in Safari, but an app fails, then SSL Pinning is probably the issue.”
感觉最大可能就是之前别人提到的:
SSL pinning
SSL探测:
app会检测你的根证书Root CA是否是自己的,此处发现(是Charles的的)而不是app自己的根证书,所以就拒绝,所以Charles就无法解密了。
如果你自己是iOS的app的开发者,想要临时放开https的限制,则可以去
1 2 3 4 5 | <key>NSAppTransportSecurity</key><dict><key>NSAllowsArbitraryLoads</key><true/></dict> |
去允许非https的请求
charles how fix ssl pinning
charles ssl not work for some https
“If you’ve set up the phone with the correct Charles certificate it may be that the App Store App is using Certificate Pinning – much like Facebook. Certificate pinning prevents the usage of even a trusted proxy like Charles from monitoring their traffic.”
先去试试:
处理后,看看
能否解密明文
不过感觉不行:
首先我Android不是7.0,不需要
其次如果https无法抓包,那么现在都看不到这些https请求
现在是能看到,且部分https能解密,部分不能
所以看来这个工具对于此处没用
所以问题转换为:
如何破解ssl pinning==certificate pinning==SSL certificate pinning
HTTPS (or TLS, the protocol used to secure the transport layer for HTTPS)
ssl pinning==certificate pinning的大概逻辑是:
app发起https请求时:
- 不仅要确认是否合法有效的host主机名
- 还要确认是否合法有效的根证书Root CA
- 此处app只认自己的证书,不认Charles的证书
- 所以Charles就无法抓这种带SSL Pinning的https的包了
那抽空去:
下载旧版本,看看之前版本能否正常使用,以及能否,万一有幸,没有加密,或者虽然加密但是(没有用ssl pinning)可以被解密
然后去:
【未解决】试试旧版本的Android的app能否绕开SSL Pinning
charles how fix ssl pinning
how fix ssl certificate pinning
“Cert pinning will prevent this from working, but that’s the only thing that will.
How do you intercept traffic from apps that use cert pinning? Is the only way to patch the app binary and reinstall the patched binary using a dev certificate?”
好像说是可以:打补丁,加上dev的证书,或许就可以解决ssl pinning的问题了?
去看看:
感觉很复杂:
都要涉及到如何破解app,破解ssl的验证方式了
“You’ll see the attempted request (the fact that there was a request to a named server) but none of the request details, except the encrypted stream.
There are guides you can google for cracking apps and replacing the certs they compare against. IIRC they all require a jailbroken device.”
抽空继续搜
貌似说是:
如果能找到本身app所使用的证书,然后想办法弄到app或Android设备中,或许就可以实现破解ssl pinning了?
“How widespread is certificate pinning nowadays in iOS apps? Does anybody have any experiences?
illuminati1911 5 months ago [-]
I’m working at a European bank in their iOS team. We use cert pinning for all of our apps, but I have never heard or seen teams using it outside of this project.
I guess it’s mostly used if the application is doing something critical like money transactions etc.
iampims 5 months ago [-]
Cert pinning seems to be gaining momentum in the US several high profile apps are using it now.”
现在用ssl pinning的app越来越多了,虽然还不是足够广泛。
“need a jailbroken device
that there are tools such as SSL Kill Switch[1]
[0] https://news.ycombinator.com/item?id=15757878 [1] https://github.com/iSECPartners/ios-ssl-kill-switch
”
需要一个越狱,破解的手机,加上工具:
需要先去给iPhone越狱,比如用Cydia ?
且要安装对应的包:
* dpkg
* MobileSubstrate
* PreferenceLoader
然后再去用这个:
ios-ssl-kill-switch
就可以绕过ssl -》 当然也就完全破解ssl pining了
其中提到了Android中的http库:
OkHttp
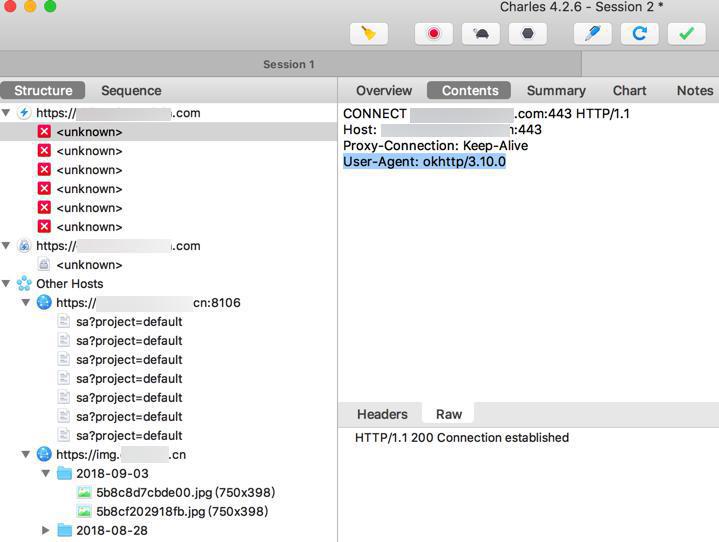
-》而之前抓包好像就是发现此趣配音app中就是用的:
User-Agent: okhttp/3.10.0
且提到了:
“OkHttp has offered certificate pinning since OkHttp 2.1.”
-》此处用的是okhttp 3.10.0,所以内部是支持ssl pinning的
后记:
在:
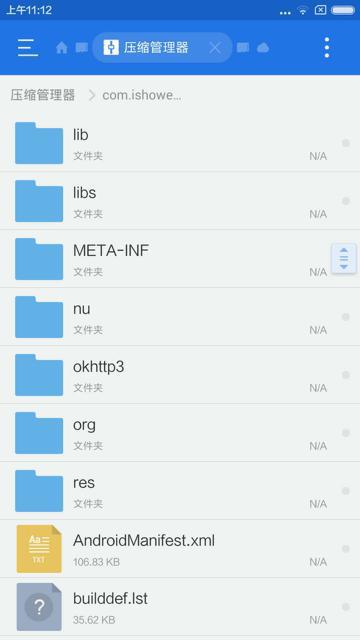
【已解决】Android手机锤子M1L中查看已安装app的目录和文件中是否有cer等证书文件
中,也看到了apk中是有OkHttp3的文件夹的:
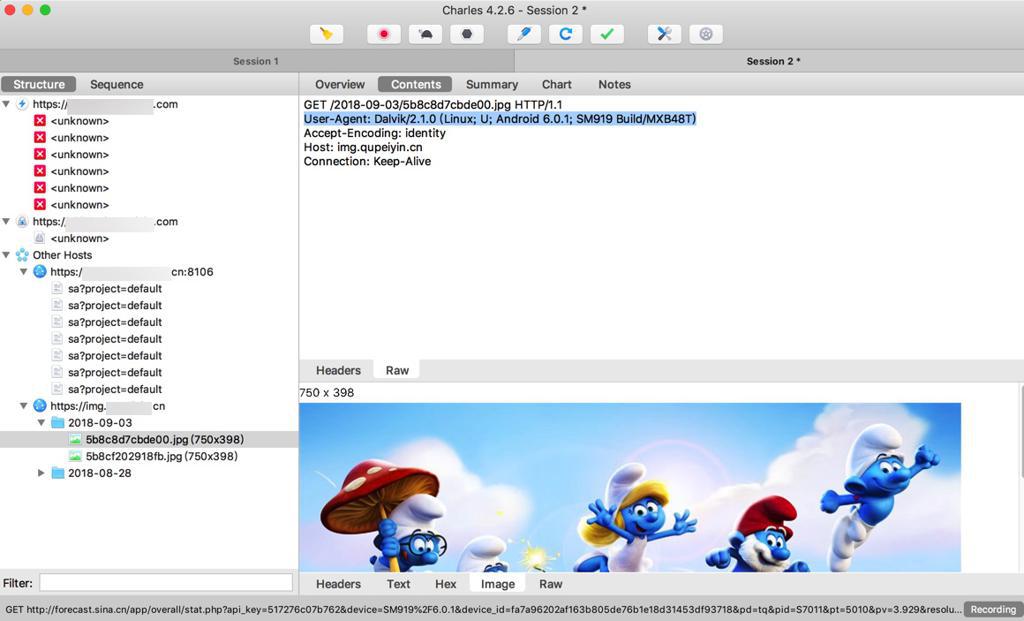
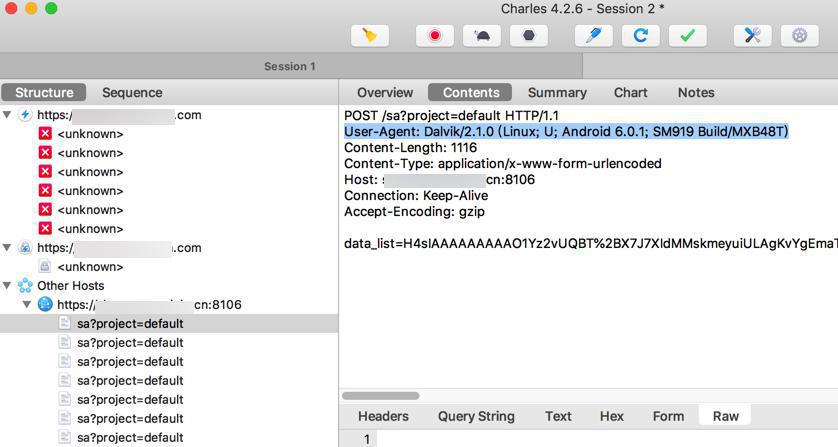
而才注意到,别的可以被解密的https请求的User-Agent是:
User-Agent: Dalvik/2.1.0 (Linux; U; Android 6.0.1; SM919 Build/MXB48T)
所以现在对于此处app在Android中利用OkHttp实现了ssl pinning来说:
问题转换为:
Android中如何破解用了OkHttp的ssl pinning的app
(后来发现:
也提到了类似的)
也提到了:
如何验证你的ssl pinning真正起效了的话,可以,在root后的Android设备中,用工具:
以及:
- Burp Suite
- OWASP ZAP
- Mitmproxy
- Fiddler
也提到了:
“With a little more technical know-how a user of your app can reverse engineer your app to disable it so they will be able to inspect the traffic. ”
可以逆向工程去破解你的apk的,禁止掉ssl,就可以破解https的包了
比如:
“SSL pinning isn’t something you want to do in all your applications, but for high-risk apps that require increased levels of security, it might just make sense.”
说了:
其实并不需要你把所有的网络请求都弄成ssl pinning
只把那些高度机密的接口弄成ssl pinning就可以了
说了,如果想要HTTP pinning==ssl pinning,常见的方式是:
- Android中:利用Android官网的
- 网络安全性配置 | Android Developers
- https://developer.android.com/training/articles/security-config.html
- iOS中:利用TrustKit
- an open-source SSL pinning library for iOS and macOS
- https://github.com/datatheorem/TrustKit
人家用到的ssl pinning方面的证书,比此处Charles的ROOT CA中:
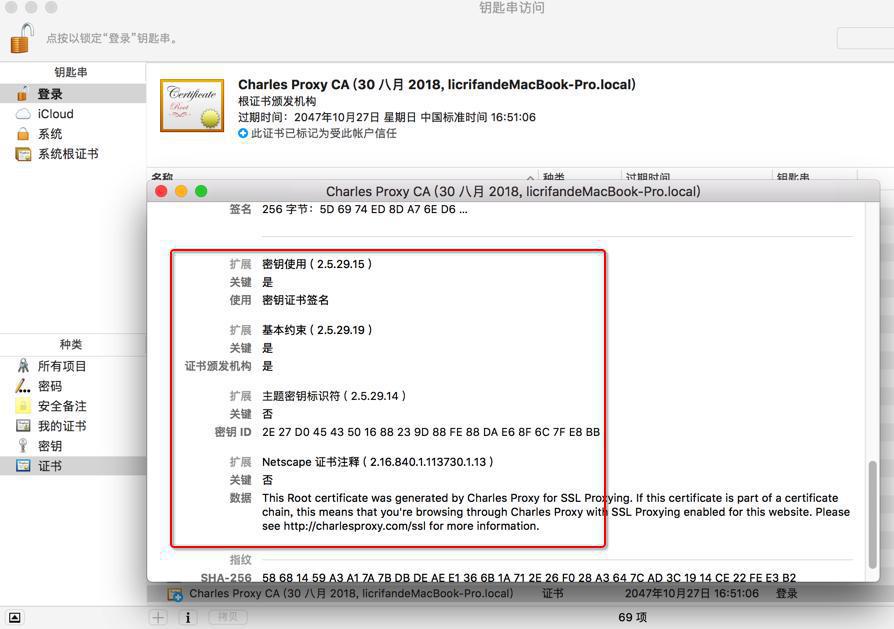
多了个:
1 2 3 4 | Extension: Extended Key UsageCritical: NoPurpose #1: Sever AuthenticationPurpose #2: Client Authentication |
提到了4种办法,绕开Android的SSL验证和 Certificate pinning
MITM==man-in-the-middle
CA=certificate authority
4种办法:
- Adding a custom CA to the trusted certificate store
- Overwriting a packaged CA cert with a custom CA cert
- Using Frida to hook and bypass SSL certificate checks
- Reversing custom certificate code
方法1:添加自定义的CA到受信任凭据中
背景知识:
Android中:
受信任的凭据:
- 系统:保存了系统预装的CA
- 用户:保存了用户安装的CA
安全连接,比如HTTPS或TLS,都默认信任来自系统预装的CA
另外:Android 6.0(API level 23)及以下,默认也信任用户安装的CA
-》其中一种破解办法:
想办法破解APP,修改其中的AndroidManifest.xml的manifest的platformBuildVersionCode为23或更小-》强制app的target目标系统版本是Android 6.0或更低 -》使得app默认信任用户安装的CA
更细节的操作,还会涉及到:
/res/xml/network_security_config.xml
-》但是很明显,要去找工具去反编译,或者自动化处理,才能修改已有apk的内部信息,重新打包才行 -》还是非常麻烦。
-》那么或许后续能把Charles的CA安装到 系统 中,或许可以绕过此app的ssl pinning?
抽空去试试,找个root的Android手机,把重命名后的Charles的root CA放到系统目录
方法2:把自定义的CA装进app中后重新打包出新apk
此处先去:
【未解决】Android手机锤子M1L中查看已安装app的目录和文件中是否有cer等证书文件
没找到cer文件,结果后来发现搞错了:
是需要用apk工具,比如APK Studio,去打开apk,才能看到cer文件
但是还是需要:
找工具破解apk,找到apk中的证书,替换为自己的证书,重新打包
-》还是需要破解,还是很麻烦。
方法3:Frida Hook
Frida Gadget
不过看起来还是很麻烦
-》还是不如用前面那些工具,比如:
Android-SSL-TrustKiller或JustTrustMe
方法4:Reversing Custom Certificate Validation Code
逆向工程,更麻烦。
总体来说:
不那么复杂的,或许可行的办法:
先去:
【已解决】安卓手机红米Redmi 5A去添加Charles的代理和安装证书
此处已经确保,红米5A和之前锤子M1L一样:
Charles的cer证书,安装后,都是 受信任凭据中
系统 中 没有
用户中 有
然后也都可以实现:
基本的https的链接,是可以正常抓取的
然后再去确认一下,此处趣配音中的特殊的https地址:
是否可以解密看到明文,结果是:
在用小米的应用市场下载 少儿趣配音期间就已经发现:
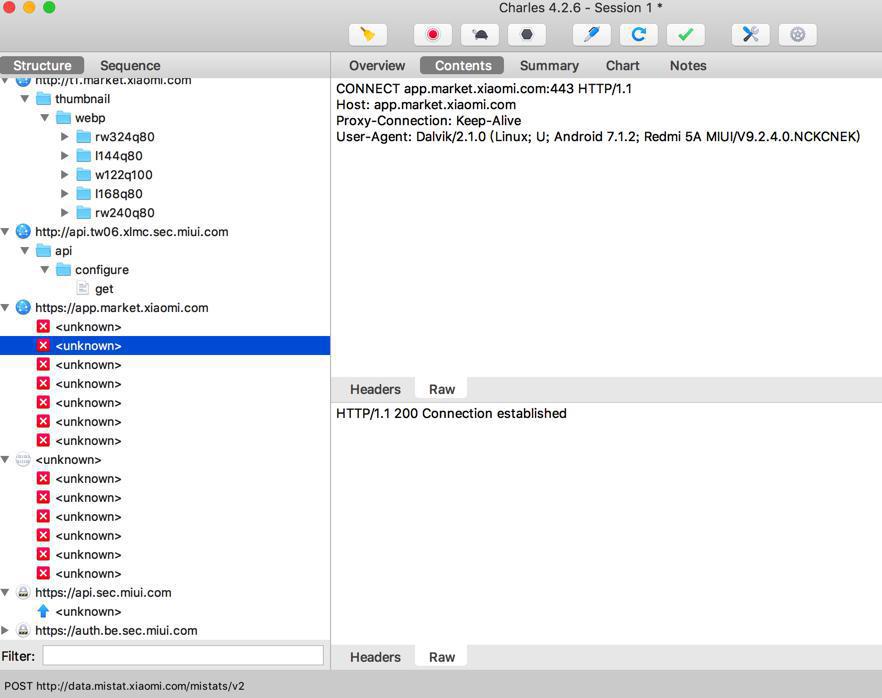
部分https是开启SSL也还是无法解密的。
所以估计上述地址也肯定没法解密。
果然问题依旧:
所以如之前所预计的,再去:
【未解决】去root安卓手机红米Redmi 5A
在满足前提:有个root后的Android手机,然后试试这些办法:
- 把重命名的证书放到 系统 中
- 禁止掉ss,规避掉ssl
- Android:用Android-SSL-TrustKiller或JustTrustMe等工具
- iOS:iOS SSL Kill Switch
后来也看到:
“解决方案:
之后可以愉快抓包。安装方法如下:
2.安卓: 手头没有安卓机,没法测试。解决方案如下:安装xposed框架、安装并启用justtrustme模块
”
我装了个安卓模拟器然后给它装xposed来抓包
-》貌似也可以
-》就不用去找root后的安卓手机了
-》据说也可以,我用的逍遥模拟器
夜神安卓模拟器 安装完毕, windows 7, 启动就crash, 什么垃圾?
【已解决】Mac中安装和使用安卓模拟器
其中:
【记录】Mac中安装网易MuMu安卓模拟器安装和使用安卓app和配置系统
然后接着去:
【未解决】Mac中用Charles抓包网易Mumu安卓模拟器中Android的app
最后是通过,夜神安卓模拟器去,通过JustTrustMe而禁止了ssl证书的检测,从而解决了问题:
使得ssl pinning的https也可以被解密看到明文了:
【已解决】Mac中用Charles抓包夜神安卓模拟器中Android的app的数据
【后记】
跑通整个流程后,再去看:
“Ensure that Cydia Substrate has been deployed on your test device”
才懂意思是:
Android-SSL-TrustKiller是个Cydia的插件
-》要你Android手机安装了Cydia Substrate(简称Cydia)这个工具,然后才能去安装基于Cydia的插件,才能实现绕过(禁止)掉ssl pinning。
转载请注明:在路上 » 【已解决】Charles无法抓包部分加了SSL Certificate Pinning的https包