折腾:
【未解决】从不同版本的小花生apk中反编译出包含业务逻辑代码的dex和jar包源码
期间,发现dex2jar去反编译,提取出的jar包期间:
1 | sh /Users/crifan/dev/dev_tool/android/reverse\ engineering/dex-tools/dex-tools-2.1-SNAPSHOT/d2j-dex2jar.sh -f com.huili.readingclub8725900.dex |
结果输出一堆的错误,详见:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 | ...WARN: can't get operand(s) for move-result-object, wrong position ?WARN: can't get operand(s) for cmpg-float, out-of-range or not initialized ?Detail Error Information in File ./com.huili.readingclub8725900-error.zipPlease report this file to one of following link if possible (any one). https://sourceforge.net/p/dex2jar/tickets/ https://bitbucket.org/pxb1988/dex2jar/issues https://github.com/pxb1988/dex2jar/issues dex2jar@googlegroups.comjava.util.IllegalFormatConversionException: d != java.lang.String at java.util.Formatter$FormatSpecifier.failConversion(Formatter.java:4302) at java.util.Formatter$FormatSpecifier.printInteger(Formatter.java:2793) at java.util.Formatter$FormatSpecifier.print(Formatter.java:2747) at java.util.Formatter.format(Formatter.java:2520) at java.util.Formatter.format(Formatter.java:2455) at java.lang.String.format(String.java:2940) at com.googlecode.d2j.smali.BaksmaliDumpOut.s(BaksmaliDumpOut.java:68) at com.googlecode.d2j.smali.BaksmaliCodeDumper.visitFilledNewArrayStmt(BaksmaliCodeDumper.java:248) at com.googlecode.d2j.node.insn.FilledNewArrayStmtNode.accept(FilledNewArrayStmtNode.java:19) at com.googlecode.d2j.smali.BaksmaliDumper.accept(BaksmaliDumper.java:569) at com.googlecode.d2j.smali.BaksmaliDumper.baksmaliCode(BaksmaliDumper.java:544) at com.googlecode.d2j.smali.BaksmaliDumper.baksmaliMethod(BaksmaliDumper.java:482) at com.googlecode.d2j.smali.BaksmaliDumper.baksmaliMethod(BaksmaliDumper.java:428) at com.googlecode.dex2jar.tools.BaksmaliBaseDexExceptionHandler.dumpMethod(BaksmaliBaseDexExceptionHandler.java:148) at com.googlecode.dex2jar.tools.BaksmaliBaseDexExceptionHandler.dumpTxt0(BaksmaliBaseDexExceptionHandler.java:126) at com.googlecode.dex2jar.tools.BaksmaliBaseDexExceptionHandler.dumpZip(BaksmaliBaseDexExceptionHandler.java:135) at com.googlecode.dex2jar.tools.BaksmaliBaseDexExceptionHandler.dump(BaksmaliBaseDexExceptionHandler.java:92) at com.googlecode.dex2jar.tools.Dex2jarCmd.doCommandLine(Dex2jarCmd.java:120) at com.googlecode.dex2jar.tools.BaseCmd.doMain(BaseCmd.java:290) at com.googlecode.dex2jar.tools.Dex2jarCmd.main(Dex2jarCmd.java:33) |
且对于最后输出的jar包,用工具查看到java代码中,包含:
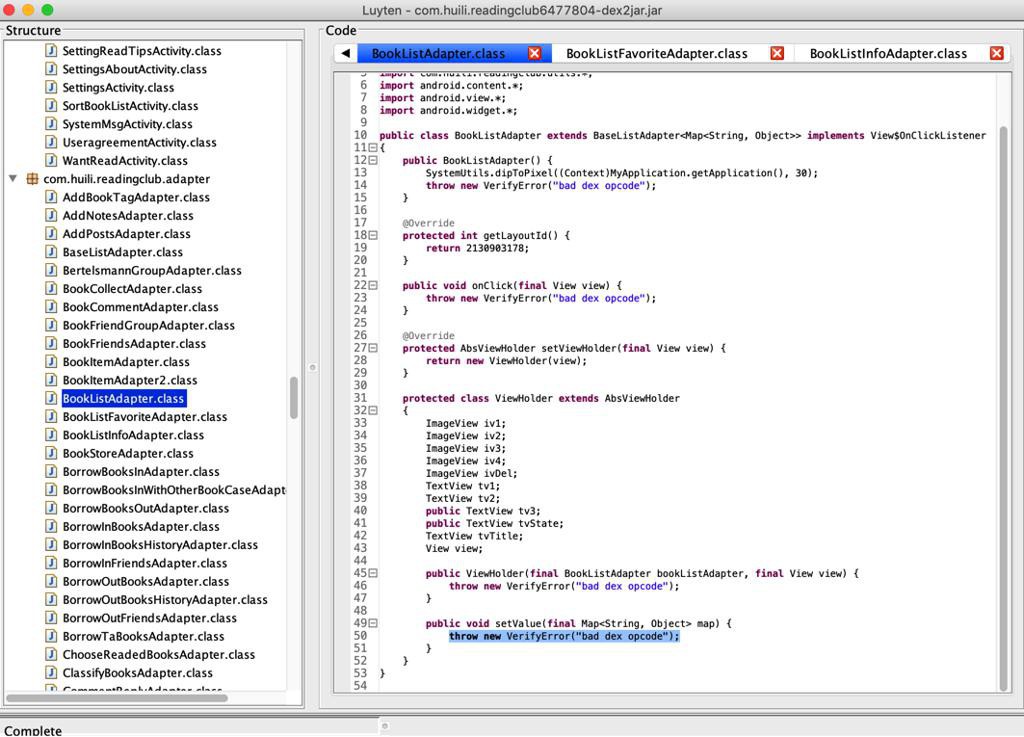
1 | throw new VerifyError("bad dex opcode"); |
去换用其他工具试试是否也会报错:
【已解决】用jadx把安卓dex文件转换提取出jar包和java源代码
虽然树状显示不错,但是代码解析效果不行,且CPU占用率高卡死,放弃。
搜一下:
dex2jar bad dex opcode
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 | tmp.init(frame);//用frame初始化tmp try { if (p.op != null) { switch (p.op) { case RETURN_VOID: emit(nReturnVoid());//添加一个ReturnVoidStmt break; case GOTO: case GOTO_16: case GOTO_32: emit(nGoto(getLabel(((JumpStmtNode) p).label))); break; case NOP: emit(nNop()); break; case BAD_OP: emit(nThrow(nInvokeNew(new Value[]{nString("bad dex opcode")}, new String[]{ "Ljava/lang/String;"}, "Ljava/lang/VerifyError;"))); break; default: tmp.execute(p, interpreter);//缺省情况执行execute tmp为Dex2IrFrame break; } } |
此处暂时无法解决。
VerifyError bad dex opcode
360加固源码分析
类com.stub.StubApp
1 2 3 4 5 6 7 8 9 10 | public class StubApp extendsApplication{... static {strEntryApplication = "com.qihoo360.crypt.entryRunApplication"; ?? = null; ?? = "libjiagu";loadFromLib = false;needX86Bridge = false; throw newVerifyError("bad dex opcode"); } |
好像此处是:360的加固?
“java.lang.VerifyError 新问题样本
1 反编译出问题的东西大部分在构造函数,init()方法大部分都出现在缺少return-void
2 当前类继承的interface,父类为java object ,出现 没有调用java object – > init()方法
对于以上问题,其实相关工具会在smali文件里面存在 #disallowed odex opcode错误,直接搜索就可以解决。”
“09-11 23:16:39.974 19298-19298/? E/AndroidRuntime: FATAL EXCEPTION: main
Process: es.malvarez.mywatchfaces, PID: 19298
java.lang.VerifyError: bad dex opcode
at com.huami.watch.watchface.util.Util.<clinit>(Unknown Source)
at com.huami.watch.watchface.AbstractWatchFace.onCreate(Unknown Source)
at android.app.ActivityThread.handleCreateService(ActivityThread.java:2761)”
apktool bad dex opcode
dex2jar bad dex opcode
” static
{
JniLib.a(Checker.class, 22);
throw new VerifyError(“bad dex opcode”);
}”
“case BAD_OP:
emit(nThrow(nInvokeNew(new Value[]{nString(“bad dex opcode”)}, new String[]{
“Ljava/lang/String;”},
“Ljava/lang/VerifyError;”)));
break;”
只是知道是BAD_OP的case,但是不知道如何破解和避免啊
dex2jar BAD_OP
“case BAD_OP:
emit(nThrow(nInvokeNew(new Value[]{nString(“bad dex opcode”)}, new String[]{
“Ljava/lang/String;”},
“Ljava/lang/VerifyError;”)));
break;”
BAD_OP(-1, “bad-opcode”, null, kIndexNone, 0, false), //
android bad dex opcode
“由于360加壳之后,更改了classloader,因此我们用原本的classloader是会报类无法被找到的异常的。
不过我们去分析源码便知道,我们要先hook到360的classloader,再从360的classloader里面获取到app运行时的类。”
还是看不太懂,如何操作才能hook出360的classloader
解释的都看不懂
去试试:WrBug的DumpDex
【已解决】用WrBug的DumpDex从app中hook导出dex文件
转载请注明:在路上 » 【未解决】dex2jar反编译dex后jar文件包含java代码:throw new VerifyError bad dex opcode