之前已经:
【部分解决】尝试破解安卓apk康美通去得到java源码
且知道,最新的360加固保和腾讯乐固,用Jadx或FDex2的方式,都无法获取到源码的。
不过也还是去试试,最新版的马蜂窝能否得到源码。
马蜂窝 app
马蜂窝 apk
马蜂窝旅游 for Android – APK Download
https://apkpure.com/马蜂窝旅游-查找旅游攻略游记点评-预订酒店机票行程/com.mfw.roadbook
9.3.0
(1)网上下载的:com.mfw.roadbook_9.3.6_730.apk
版本:9.3.6
-》竟然能,直接用Jadx反编译出来
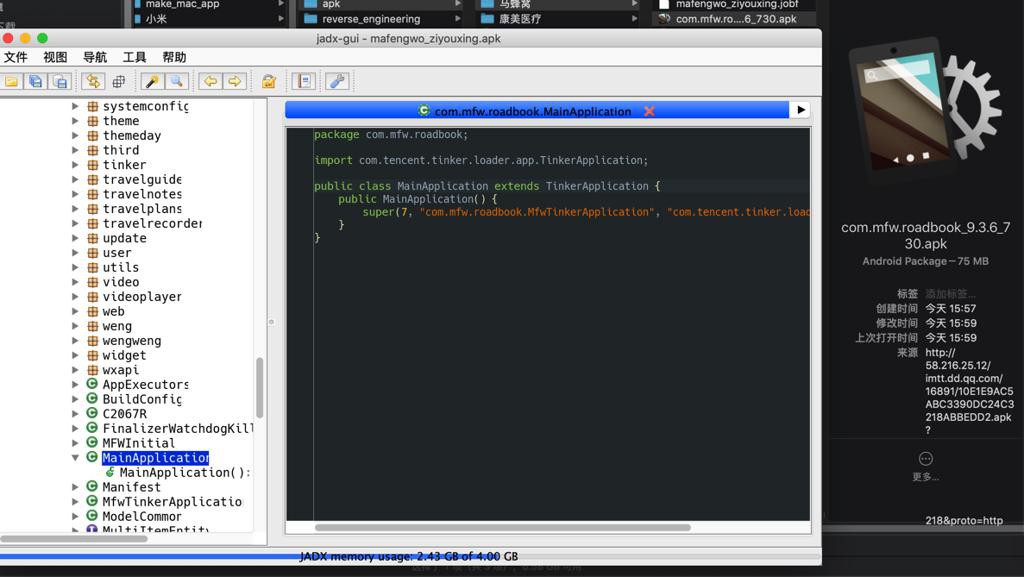
-》内部版本号好像是9.3.2
(2)官网最新版本的:mafengwo_ziyouxing.apk
也是可以用jadx直接反编译看到java源码的:
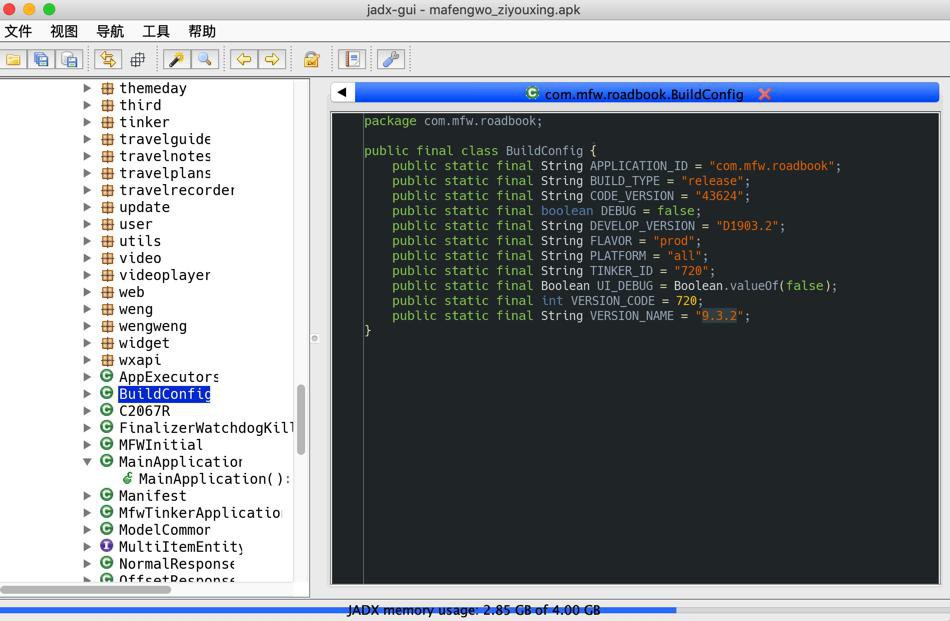
内部也是9.3.2
com.mfw.roadbook.BuildConfig
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 | package com.mfw.roadbook;public final class BuildConfig { public static final String APPLICATION_ID = "com.mfw.roadbook"; public static final String BUILD_TYPE = "release"; public static final String CODE_VERSION = "43624"; public static final boolean DEBUG = false; public static final String DEVELOP_VERSION = "D1903.2"; public static final String FLAVOR = "prod"; public static final String PLATFORM = "all"; public static final String TINKER_ID = "720"; public static final Boolean UI_DEBUG = Boolean.valueOf(false); public static final int VERSION_CODE = 720; public static final String VERSION_NAME = "9.3.2";} |
不过很多代码,的确是无法完美破解出来,有很多unicode和其他出错的代码
然后去用jadx命令行去导出代码看看
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 | ➜ 马蜂窝 /Users/crifan/dev/dev_tool/android/reverse_engineering/jadx/jadx-0.9.0/bin/jadx -d exported_java_src mafengwo_ziyouxing.apkINFO - loading ...ERROR - Zip bomb attack detected, invalid sizes: compressed 146, uncompressed 21896, name assets/map_assets/dash.dataERROR - Zip bomb attack detected, invalid sizes: compressed 215, uncompressed 21896, name assets/map_assets/dash_cd.dataERROR - Zip bomb attack detected, invalid sizes: compressed 146, uncompressed 21896, name assets/map_assets/dash.dataERROR - Zip bomb attack detected, invalid sizes: compressed 215, uncompressed 21896, name assets/map_assets/dash_cd.dataINFO - processing ...ERROR - Failed to decode 9-patch png image, path: assets/infowindow_bg.9.pngjadx.core.utils.exceptions.JadxException: Cant find nine patch chunk at jadx.core.utils.android.Res9patchStreamDecoder.find9patchChunk(Res9patchStreamDecoder.java:80) at jadx.core.utils.android.Res9patchStreamDecoder.getNinePatch(Res9patchStreamDecoder.java:69) at jadx.core.utils.android.Res9patchStreamDecoder.decode(Res9patchStreamDecoder.java:47) at jadx.api.ResourcesLoader.decodeImage(ResourcesLoader.java:117) at jadx.api.ResourcesLoader.loadContent(ResourcesLoader.java:104) at jadx.api.ResourcesLoader.lambda$loadContent$0(ResourcesLoader.java:82) at jadx.api.ResourcesLoader.decodeStream(ResourcesLoader.java:71) at jadx.api.ResourcesLoader.loadContent(ResourcesLoader.java:82) at jadx.api.ResourceFile.loadContent(ResourceFile.java:60) at jadx.core.xmlgen.ResourcesSaver.run(ResourcesSaver.java:32) at java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1142) at java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:617) at java.lang.Thread.run(Thread.java:745)Caused by: java.io.EOFException: null at java.io.DataInputStream.readInt(DataInputStream.java:392) at jadx.core.utils.android.DataInputDelegate.readInt(DataInputDelegate.java:61) at jadx.core.utils.android.Res9patchStreamDecoder.find9patchChunk(Res9patchStreamDecoder.java:78) ... 12 common frames omittedWARN - Finally extract failed: remBlock pred: B:10:0x0033, [B:9:0x002a, B:8:0x0028], method: android.arch.lifecycle.ComputableLiveData.2.run():voidWARN - Undo finally extract visitor, mth: android.support.v4.app.FragmentManagerImpl.execPendingActions():booleanjadx.core.utils.exceptions.JadxRuntimeException: Block not found by B:7:0x001d, in BRI{start: (B:6:0x0018, B:8:0x001e), end: (B:6:0x0018, B:8:0x001e), processed: [(B:6:0x0018, B:8:0x001e)], outs: [(B:6:0x0018, B:8:0x001e)], regMap: {}, split: 0-1}...... |
结果报错很多很多。。。
随便搜了下:
jadx ERROR Zip bomb attack detected invalid sizes compressed uncompressed
“A zip bomb, also known as a zip of death or decompression bomb, is a malicious archive file designed to crash or render useless the program or system reading it.
This is a small script written in Python which generates such a zip bomb. It is based on this repo but it receives uncompressed size as input and provides two modes: nested and flat.”
“A zip bomb, also known as a zip of death or decompression bomb, is a malicious archive file designed to crash or render useless the program or system reading it.”
看来是apk做了加密和安全处理,使得你无法简单的解压缩,否则会导致此处的zip bomb
另外,后续还有一堆其他错误:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 | WARN - Missing block: B:12:0x0038, code skipped: if (kotlin.jvm.internal.Intrinsics.areEqual(r2.tabInfo, r3.tabInfo) != false) goto L_0x003a; in method: com.mfw.roadbook.response.qa.GetQARecommendListResponse.QARecommendListEx.equals(java.lang.Object):boolean, dex: classes4.dexWARN - Wrong object literal: 1 for type: java.lang.ObjectWARN - Wrong object literal: 2 for type: java.lang.ObjectWARN - Wrong object literal: 3 for type: java.lang.ObjectWARN - Missing block: B:18:0x0056, code skipped: if (kotlin.jvm.internal.Intrinsics.areEqual(r2.bottomSmilingRightText, r3.bottomSmilingRightText) != false) goto L_0x0058; in method: com.mfw.roadbook.response.qa.QAHomeListNoteTheme.NoteThemePackageItem.equals(java.lang.Object):boolean, dex: classes4.dexWARN - Missing block: B:6:0x001a, code skipped: if (kotlin.jvm.internal.Intrinsics.areEqual(r2.list, r3.list) != false) goto L_0x001c; in method: com.mfw.roadbook.response.qa.QAHomeListNoteTheme.equals(java.lang.Object):boolean, dex: classes4.dexWARN - Missing block: B:10:0x002e, code skipped: if (kotlin.jvm.internal.Intrinsics.areEqual(r2.imgHeight, r3.imgHeight) != false) goto L_0x0030; in method: com.mfw.roadbook.response.qa.QAHomeListCommonBannerListModel.QAHomeCommonBannerItem.equals(java.lang.Object):boolean, dex: classes4.dexWARN - Missing block: B:4:0x0010, code skipped: if (kotlin.jvm.internal.Intrinsics.areEqual(r2.list, ((com.mfw.roadbook.response.qa.QAHomeListCommonBannerListModel) r3).list) != false) goto L_0x0012; in method: com.mfw.roadbook.response.qa.QAHomeListCommonBannerListModel.equals(java.lang.Object):boolean, dex: classes4.dex...WARN - Removed duplicated region for block: B:230:0x0429 in method: com.mfw.roadbook.user.collection.collection.CollectionListAdapter.bindTag(com.mfw.roadbook.adapter.base.MfwRecyclerVH, com.mfw.roadbook.response.user.CollectionModel, int):void, dex: classes4.dex... |
其中可见都是:
com.mfw.roadbook
的代码,比如:
com.mfw.roadbook.response.qa.QAHomeListCommonBannerListModel.QAHomeCommonBannerItem.equals
转换耗时很长,大概有10多分钟后,最后报错:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 | java.lang.OutOfMemoryError: GC overhead limit exceeded at jadx.core.dex.visitors.blocksmaker.BlockProcessor.computeDominators(BlockProcessor.java:189) at jadx.core.dex.visitors.blocksmaker.BlockProcessor.processBlocksTree(BlockProcessor.java:52) at jadx.core.dex.visitors.blocksmaker.BlockProcessor.visit(BlockProcessor.java:42) at jadx.core.dex.visitors.DepthTraversal.visit(DepthTraversal.java:27) at jadx.core.dex.visitors.DepthTraversal.lambda$visit$1(DepthTraversal.java:14) at jadx.core.dex.visitors.DepthTraversal$$Lambda$19/469590976.accept(Unknown Source) at java.util.ArrayList.forEach(ArrayList.java:1249) at jadx.core.dex.visitors.DepthTraversal.visit(DepthTraversal.java:14) at jadx.core.ProcessClass.process(ProcessClass.java:32) at jadx.api.JadxDecompiler.processClass(JadxDecompiler.java:292) at jadx.api.JavaClass.decompile(JavaClass.java:62) at jadx.api.JadxDecompiler.lambda$appendSourcesSave$0(JadxDecompiler.java:200) at jadx.api.JadxDecompiler$$Lambda$13/1425454633.run(Unknown Source) at java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1142) at java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:617) at java.lang.Thread.run(Thread.java:745)... |
干脆终止算了。因为也十分消耗CPU,导致CPU占用率奇高,Mac卡死了。
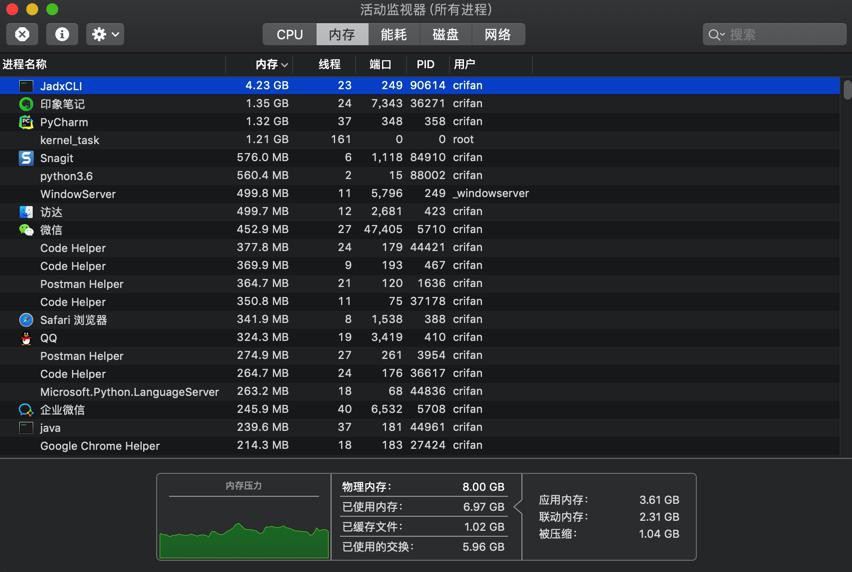
发现JadxCLI消耗了4G多内存。。。
应该是转换期间错误太多,导致消耗内存太多。
后记:
对于OOM=Out Of Memory的问题,参考
后续可以去
修改:
/Users/crifan/dev/dev_tool/android/reverse_engineering/jadx/jadx-0.9.0/bin/jadx
去把:
1 | DEFAULT_JVM_OPTS='"-Xms128M" "-Xmx4g"' |
改为:
1 | DEFAULT_JVM_OPTS='"-Xms128M" "-Xmx6g"' |
【整理】JVM参数-Xms和-Xmx参数的含义
-》自己从名字中猜测出:
- ms=memory small=最少内存
- mx=memory max=最大内存
-》不过之前最大内存已经弄到了4G了,对于当前电脑是8G内存,设置6G,也足够大了。应该够下次用了。
如果还是不行,再去:
“1、减少处理的线程数。”
用:
1 | jadx -d output_folder -j 1 your_apk.apk |
用:
- -j 1
- 指定进程数,并发数是1
- 否则默认是4
- 进程数越大,越消耗内存
- 对于OOM问题,通过减少进程数,虽然处理速度慢点,但是应该可以避免OOM了
不过此处也是转换出很多代码了:
其中有我们要的部分代码:
sources/com/mfw/roadbook
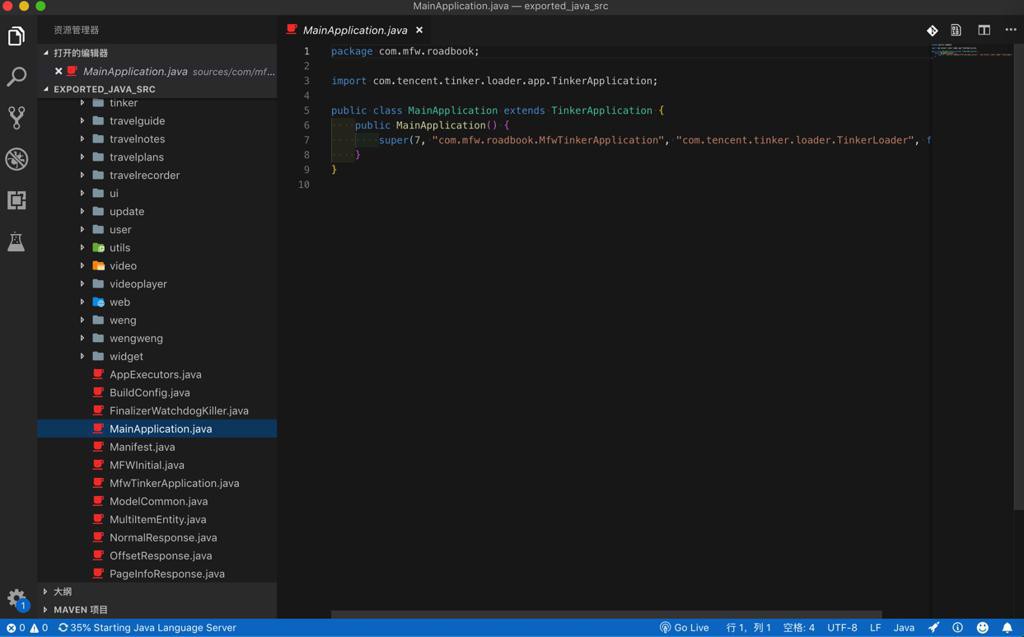
也去看看其他代码:
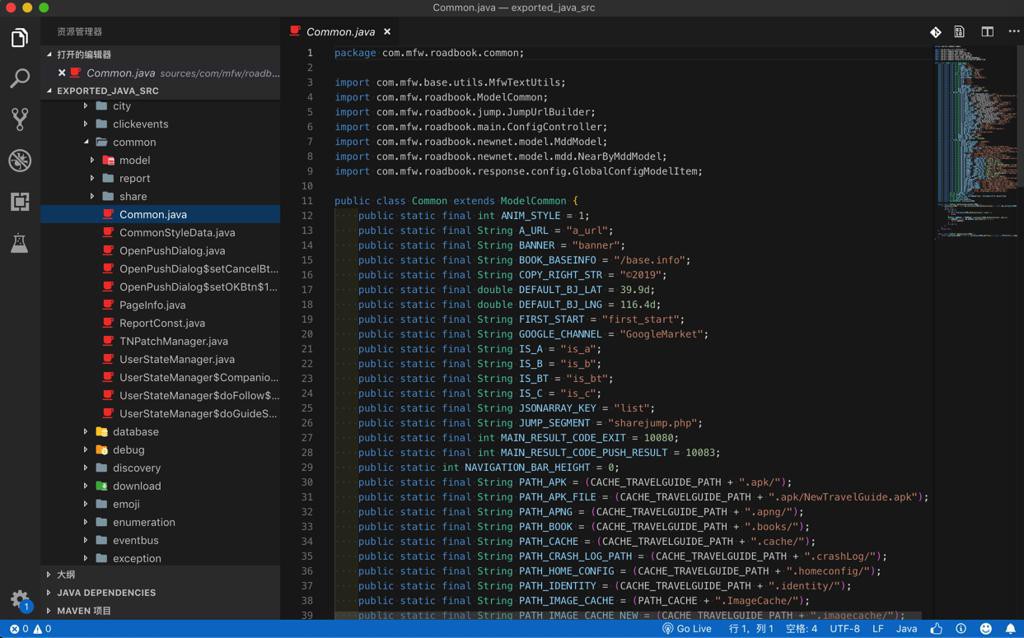
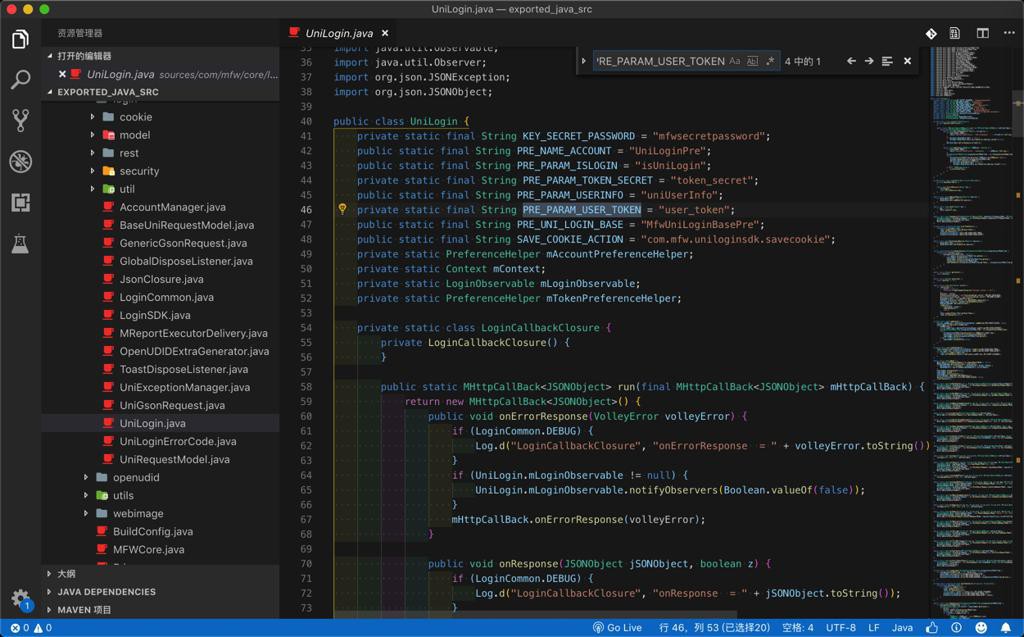
等等。
感觉算是还原出大部分的,或者说很多的,源码,虽然中间报错很多。
转载请注明:在路上 » 【基本解决】尝试破解安卓apk马蜂窝去得到java源码